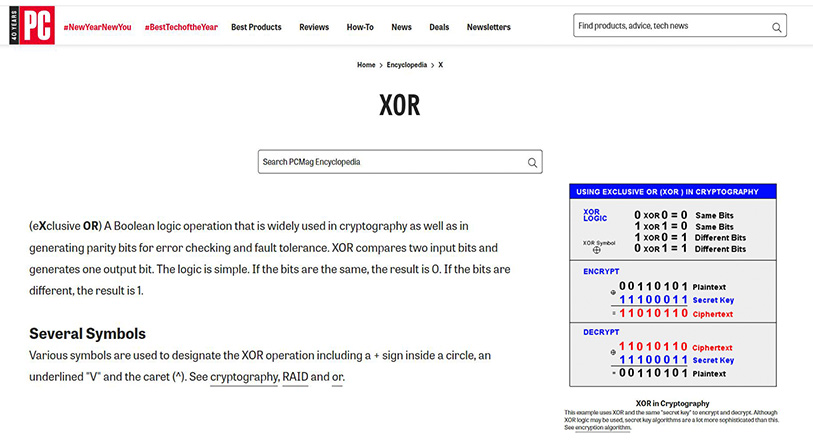
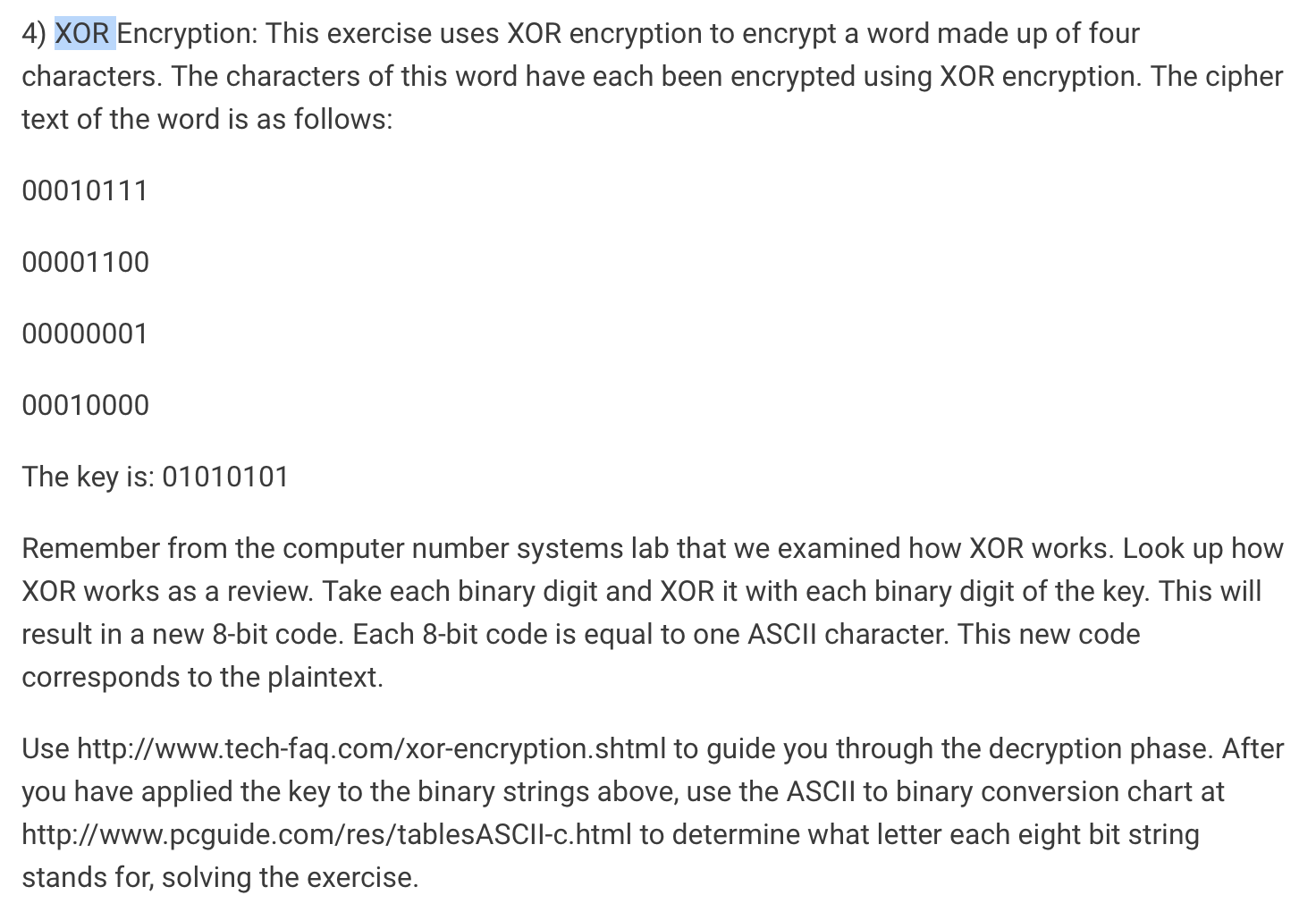
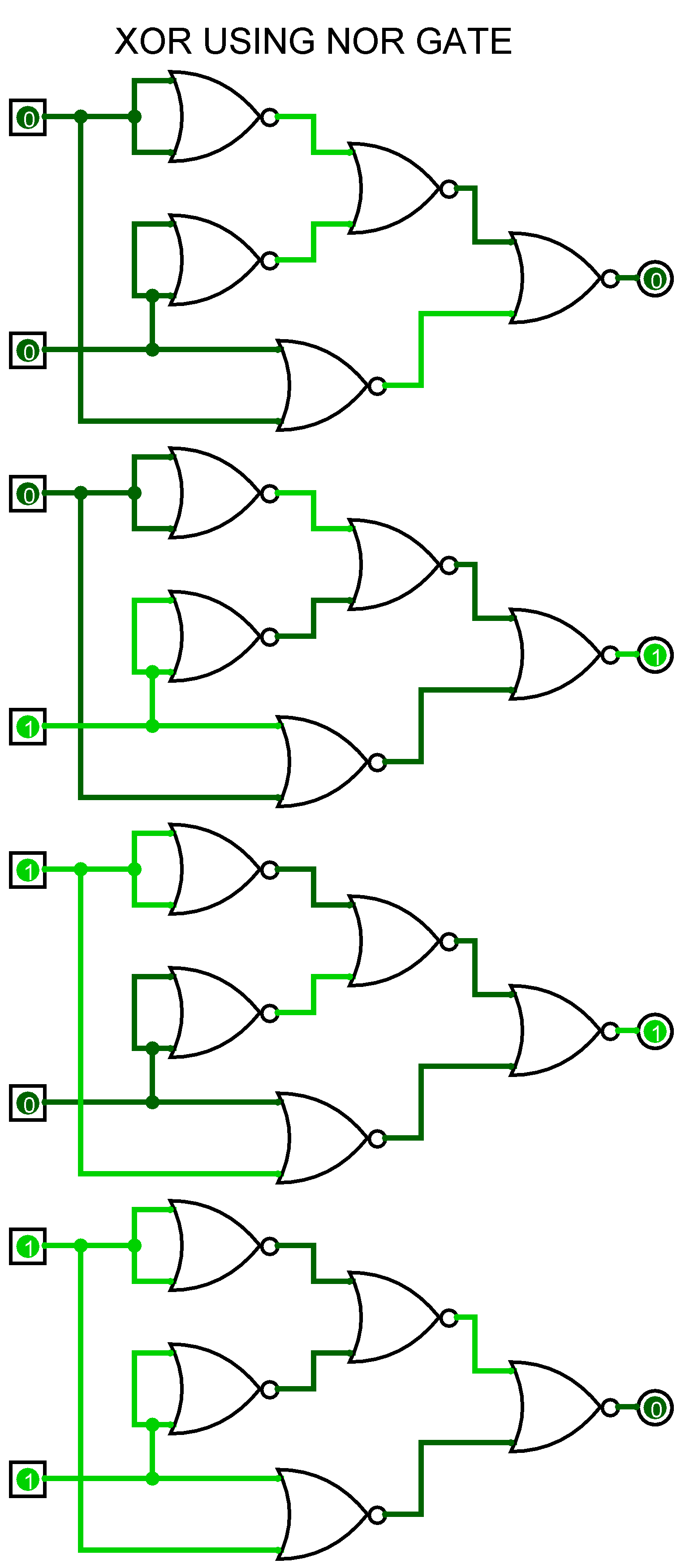
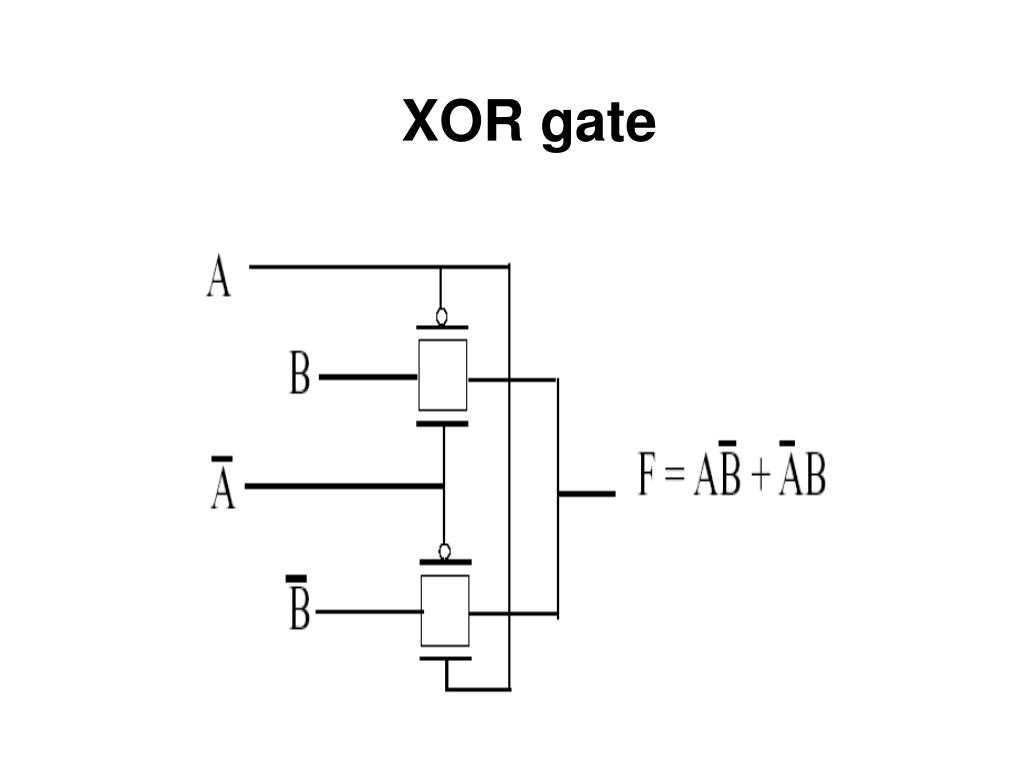
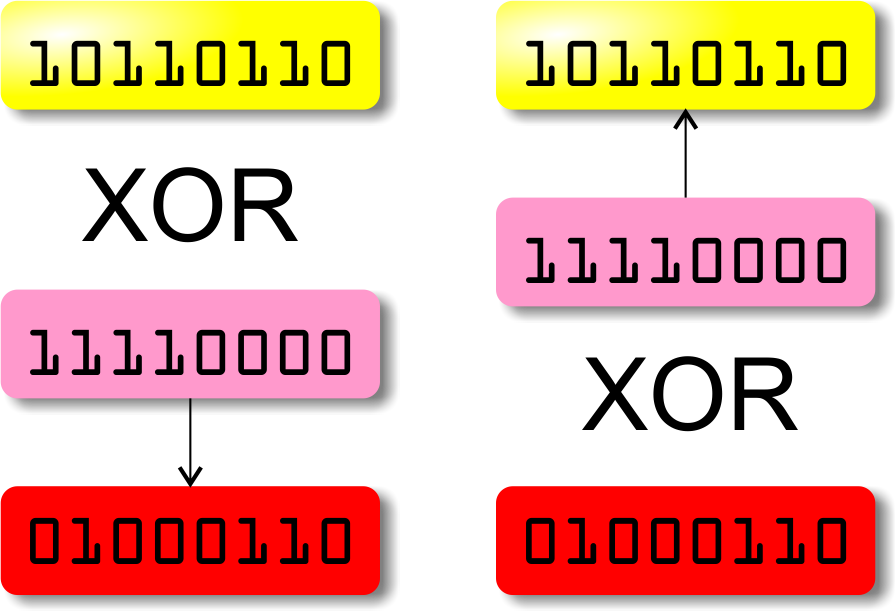
XOR encryption Andi Fugard
GitHub AlexFSmirnov xor decrypt A tool for decrypting the XOR cipher
XOR Meaning 187 Slang term definition amp example usage 187 Slang org
Why Is XOR the Perfect Cipher HackerNoon
Deciphering Single byte XOR Ciphertext
Xor operator image hi res stock photography and images Alamy
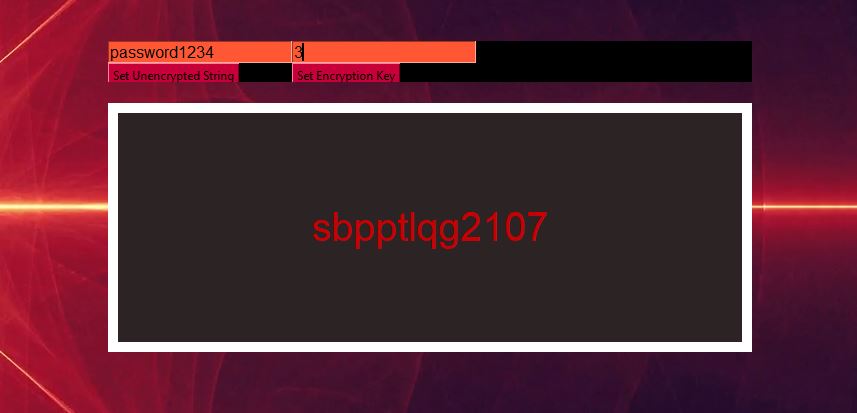
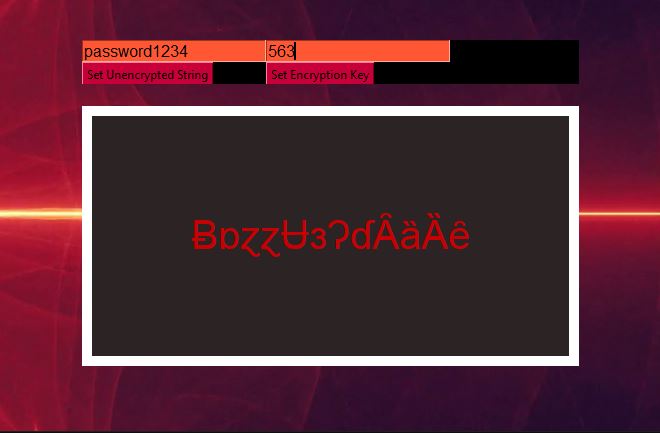
XOR Password Encryption GUI Part 1 Patrick Story
XOR Password Encryption GUI Part 1 Patrick Story
antecipate Protecting identities with XOR
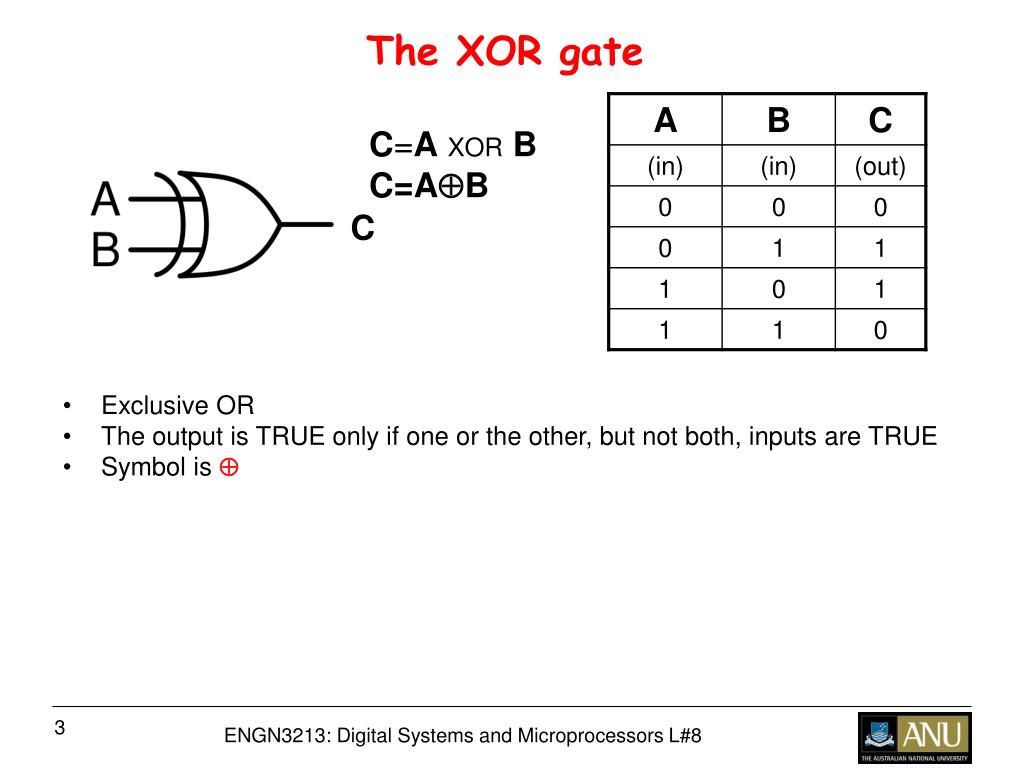
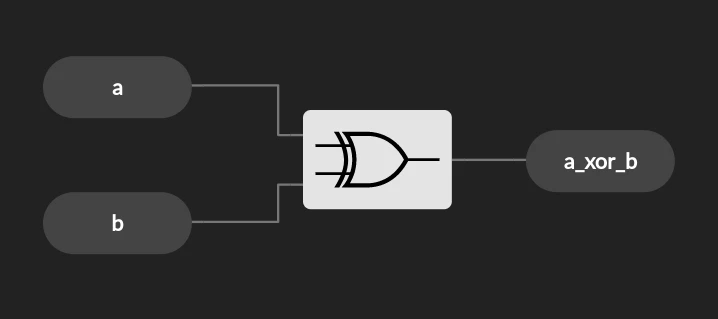
Demo The XOR Gate Learn FPGA Easily
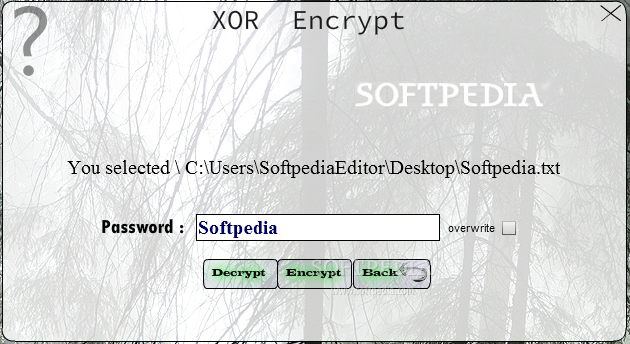
XOR Encrypt 2 0 Alpha Download Review Screenshots
XOR Encrypt 2 0 Alpha Download Review Screenshots
Symbol of XOR Unlocking the Secrets of the Exclusive OR
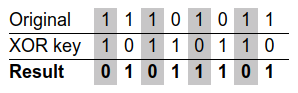
XOR Encryption and Decryption
SOLUTION Encryption xor operation Studypool
XOR Based SQL Attacks What Are They and How Do They Work
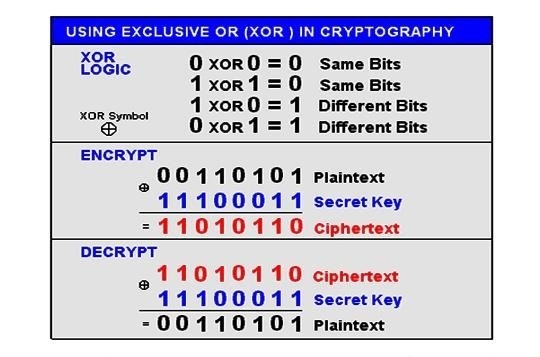
How Does XOR Cipher Work XOR Chipher Encryption by Logsign Medium
Combination of XOR encryption with LFSR Download Scientific Diagram
Hide Strings with One Key XOR Cyber Security Architect Red Blue
XOR Based SQL Attacks What Are They and How Do They Work
How Does XOR Cipher Work XOR Chipher Encryption by Logsign Medium
Combination of XOR encryption with LFSR Download Scientific Diagram
Hide Strings with One Key XOR Cyber Security Architect Red Blue
XOR and XNOR Implementation Using JavaScript UltraNewsTV
The Reason XOR is so Special in Cryptography HackerNoon
Solved 4 XOR Encryption This exercise uses XOR encryption Chegg com
Encryption implementations using a XOR based logic encryption of a
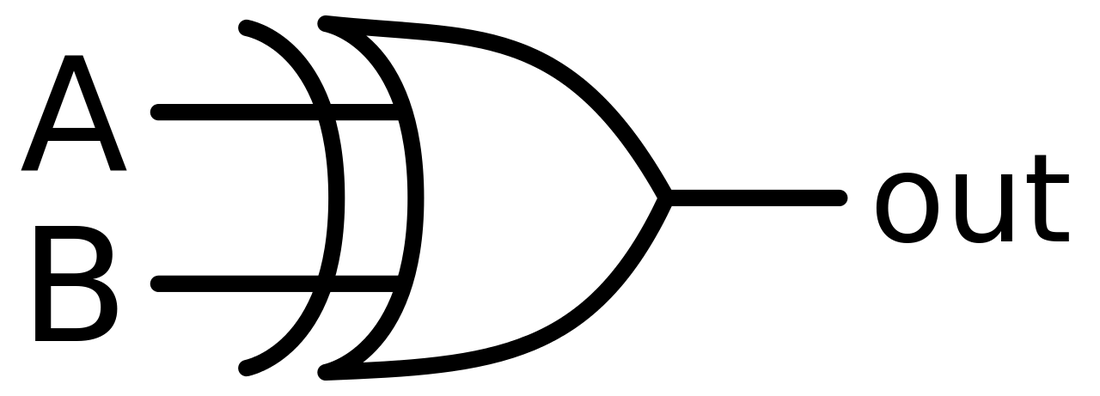
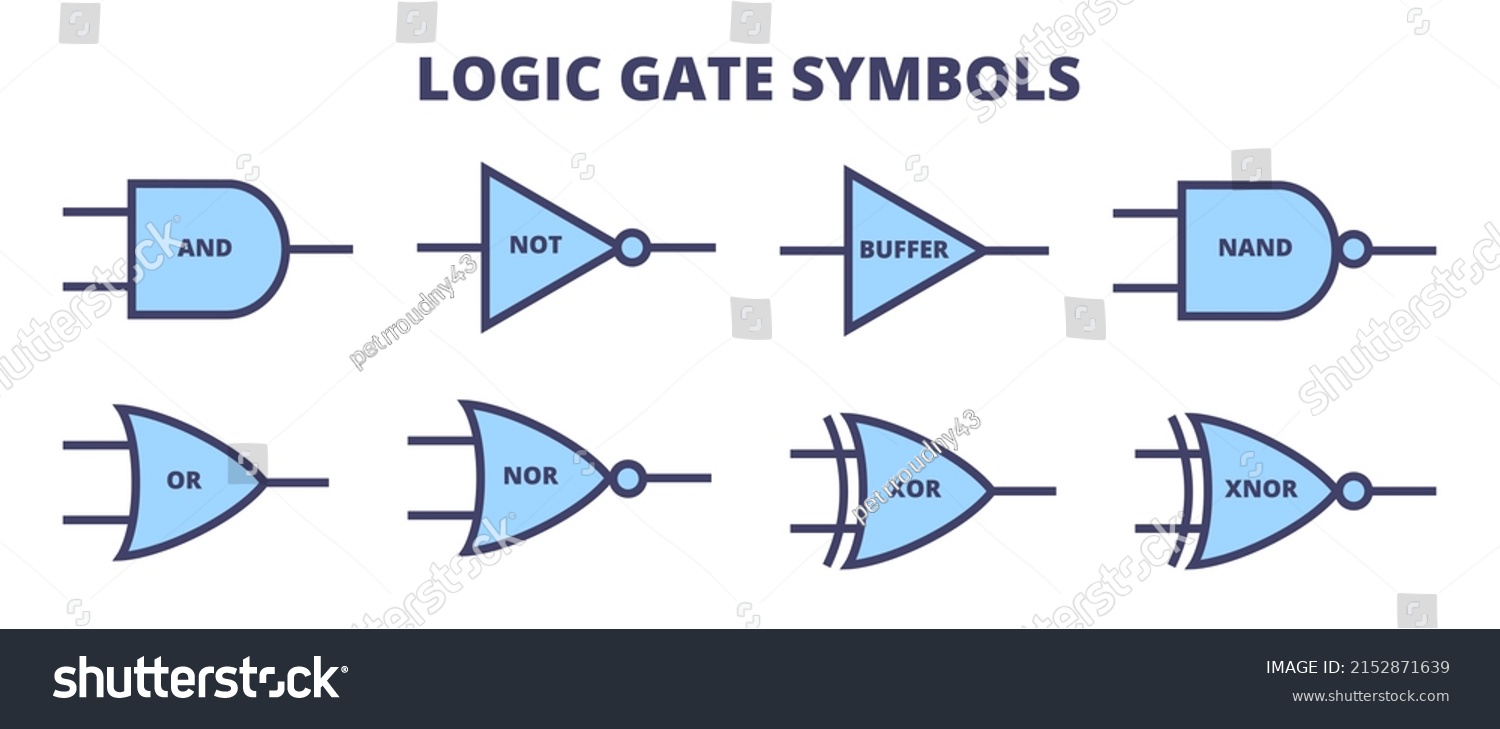
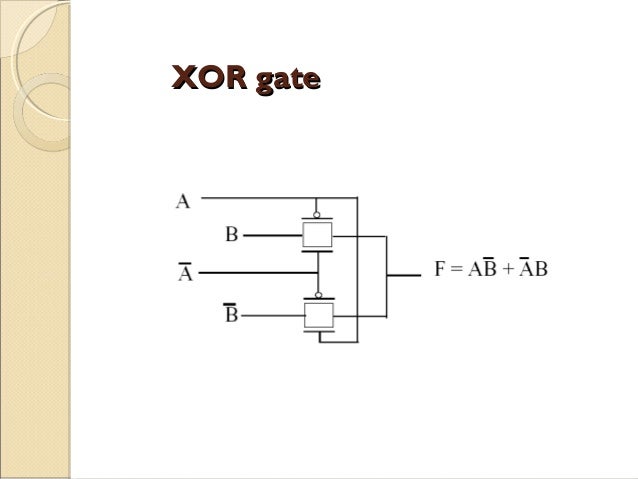
Exclusive OR gate XOR Working Principle amp Circuit Diagram
encryption Why is XOR used in cryptography Stack Overflow
Cracking repeating XOR key crypto Security Boulevard
Solved I was wondering if anyone could explain how the Chegg com
Introduction to XOR Gate projectiot123 Technology Information Website
Decrypting and spoofing a XOR encrypted cookie Najam R Syed
NQ Mobile Vault Encryption App Uses Unreliable XOR to Lock Data
Malware Basics Understanding the XOR Cipher by Devin Jun 2022
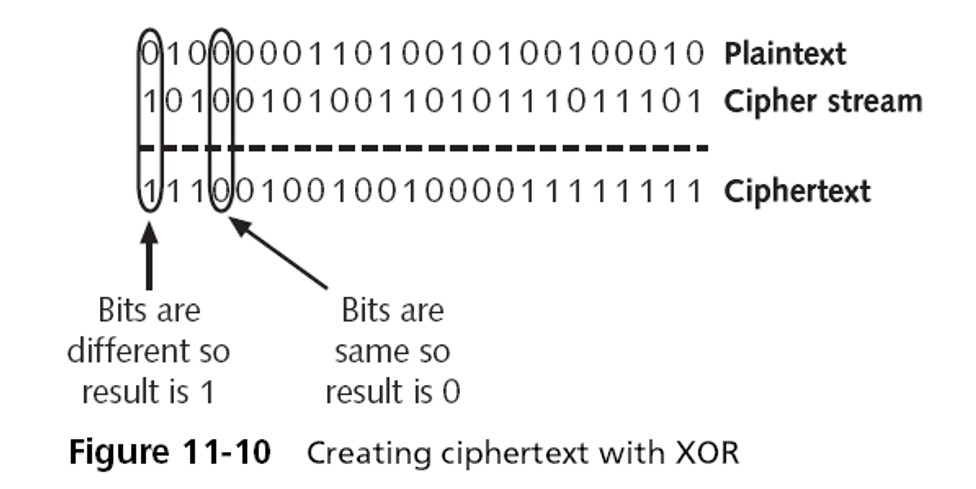
Some examples for the XOR encryption process of different characters
XOR operation between State and key word Download Scientific Diagram
encryption Why is XOR used in cryptography Stack Overflow
187 Why XOR alone is an incredibly bad encryption technique
187 Why XOR alone is an incredibly bad encryption technique
187 Why XOR alone is an incredibly bad encryption technique
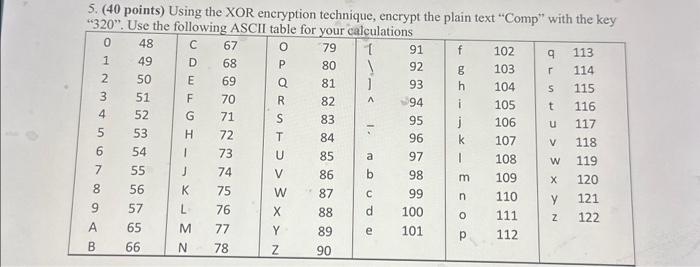
Solved 5 40 points Using the XOR encryption technique Chegg com
Solved The example above shows how to use XOR operator to Chegg com
187 Why XOR alone is an incredibly bad encryption technique
187 Why XOR alone is an incredibly bad encryption technique
Solved 5 40 points Using the XOR encryption technique Chegg com
Solved The example above shows how to use XOR operator to Chegg com
Images after xor of encrypted images with different keys and same keys
The XOR Encryption algorithm is a effective and easy to implement
The making of the XOR cipher Mathematical proof that m m k
21 Unique Xor Gate Circuit Diagram
I m assuming you use the XOR gate encryption Please write a Python
The XOR Encryption algorithm A effective and easy to implement method
Rahasia Keamanan Data dengan Cipher XOR yang Tak Terpecahkan Pintu News
Enkripsi sederhana berbasis arduino Improve XOR Semesin
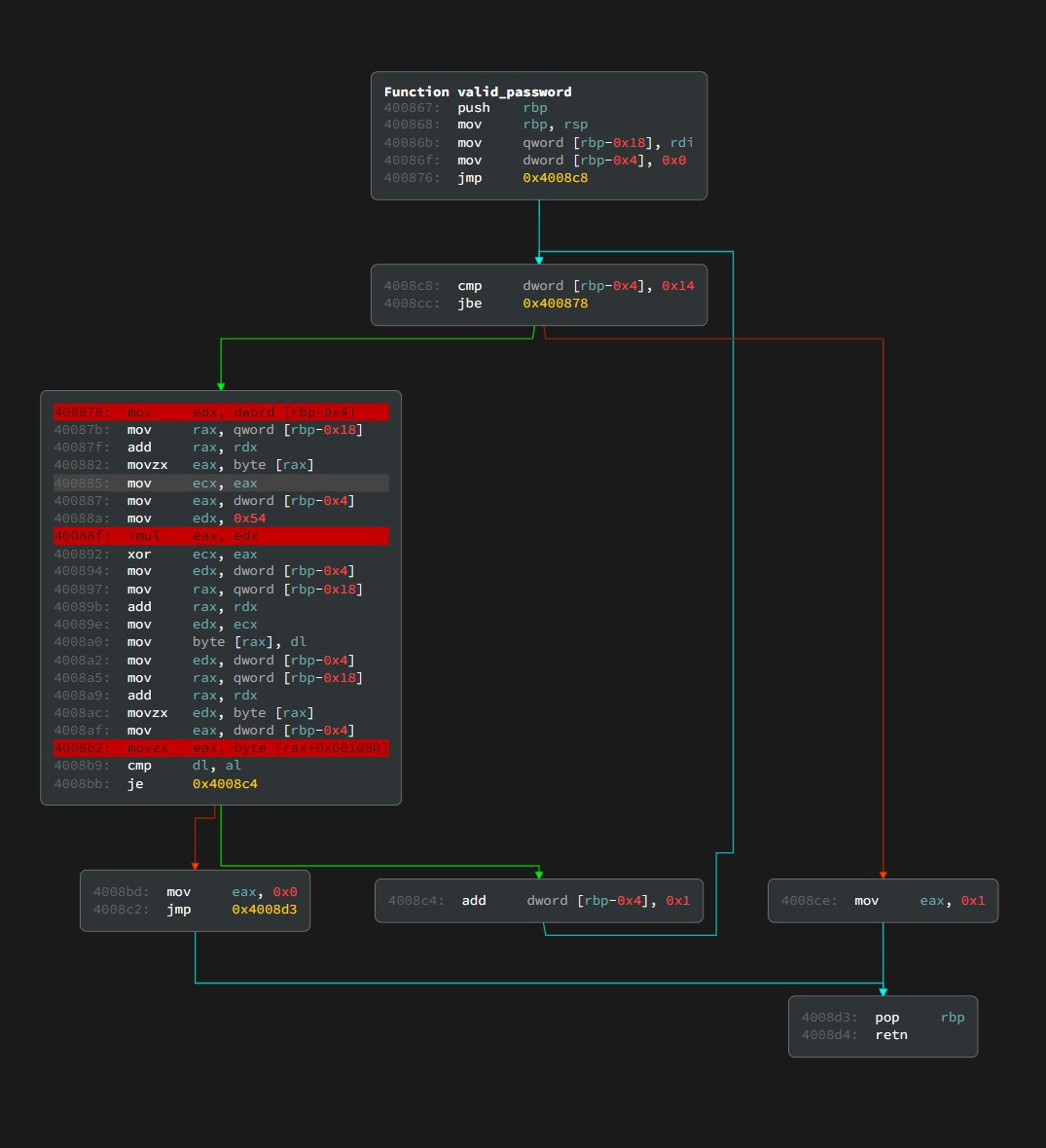
Cracking a Password Via a Side Channel
Symmetric Key Cryptography The XOR Cipher YouTube
03 XOR Cipher Keyword YouTube
01 XOR Cipher Introduction YouTube
C Why is the xor operator used in computing hash code YouTube
XOR Bitwise Operator CS201 C Tutorial for beginners Urdu XOR
XOR 3 Layer Password Guide YouTube
Two separate entries for XOR Cipher 183 Issue 193 183 TheAlgorithms
GitHub amaitou Xorcry Simple encryption tool designed to perform a
Xor 2 Download Screenshots
xor encryption Cryptography Computer technology Algebra formulas
Function Of Logic Circuit Wiring Diagram
What Is Xor Password - The pictures related to be able to What Is Xor Password in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.