How to set SLA for vulnerability management with Lansweeper
Vulnerability SLA SLO OKr Part 1 Appsec Cloudsec Infrasec amp Maturity
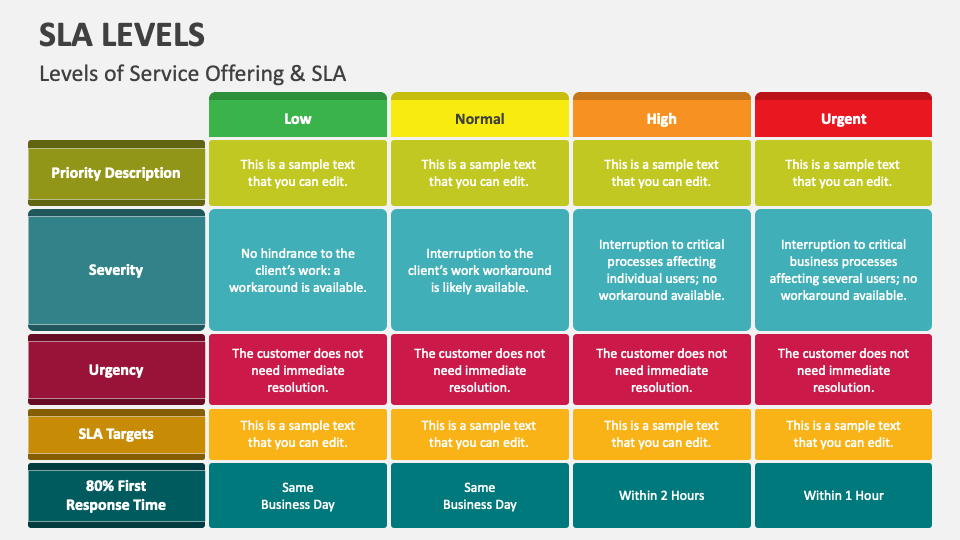
SLA Levels PowerPoint and Google Slides Template PPT Slides
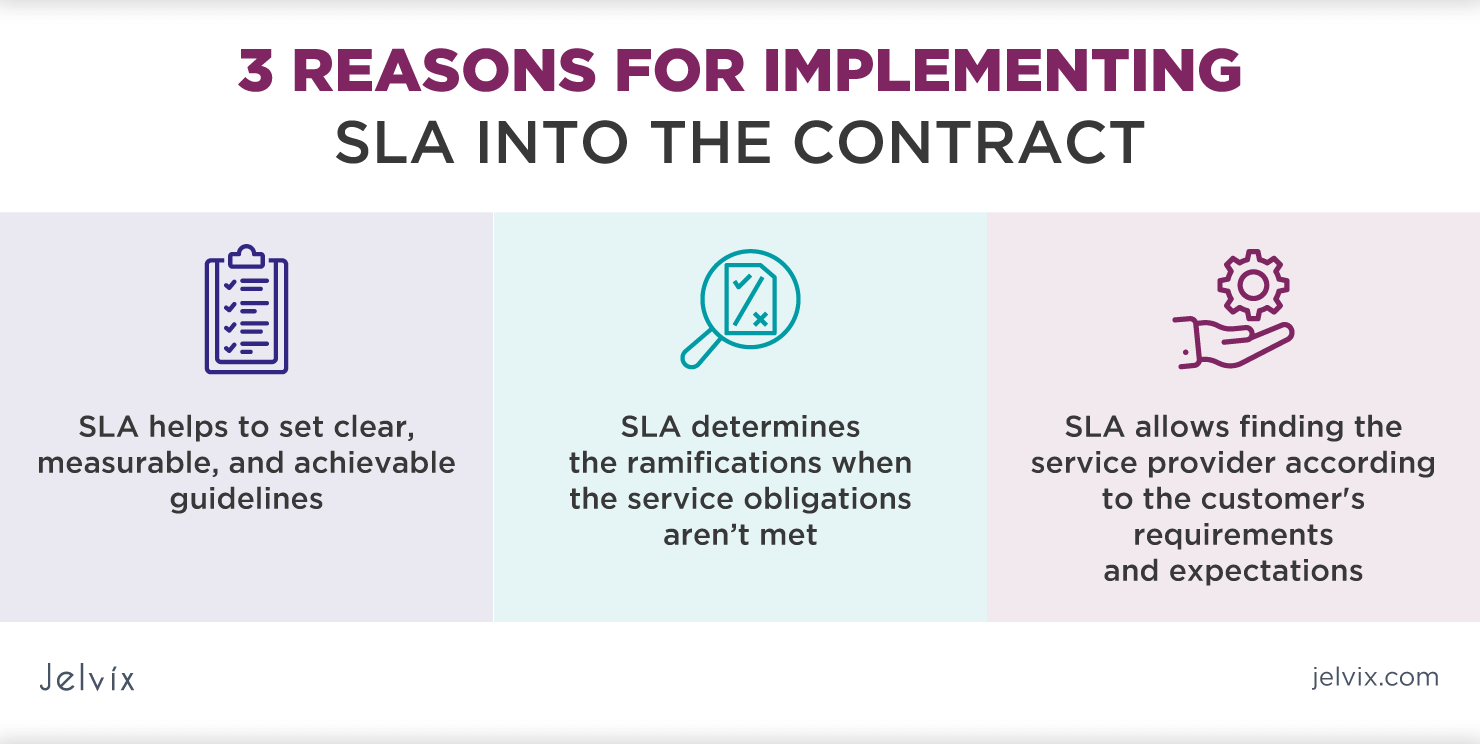
The Importance of Vulnerability Management SLA s
What does Service Level Agreement SLA Mean in Tech Sales
What does Service Level Agreement SLA Mean in Tech Sales
Key Strategies to Prevent SLA Breaches Luigi s Box
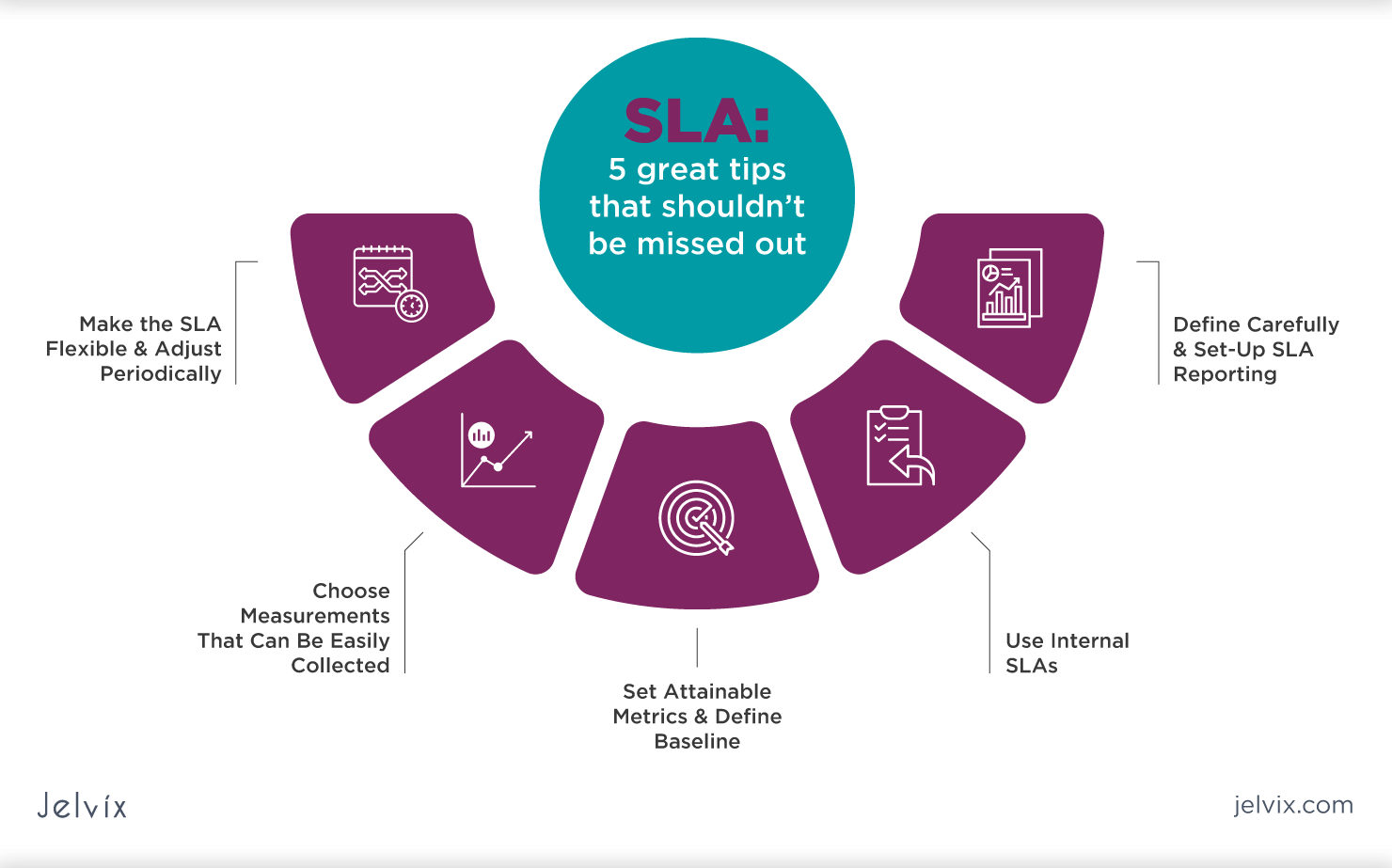
What is SLA amp How Can it Benefit Your Business Development
What is SLA amp How Can it Benefit Your Business Development
What is SLA amp How Can it Benefit Your Business Development
What is SLA Service Level Agreement Alloy Software
Setting Standards Vulnerability Management SLA Best Practices
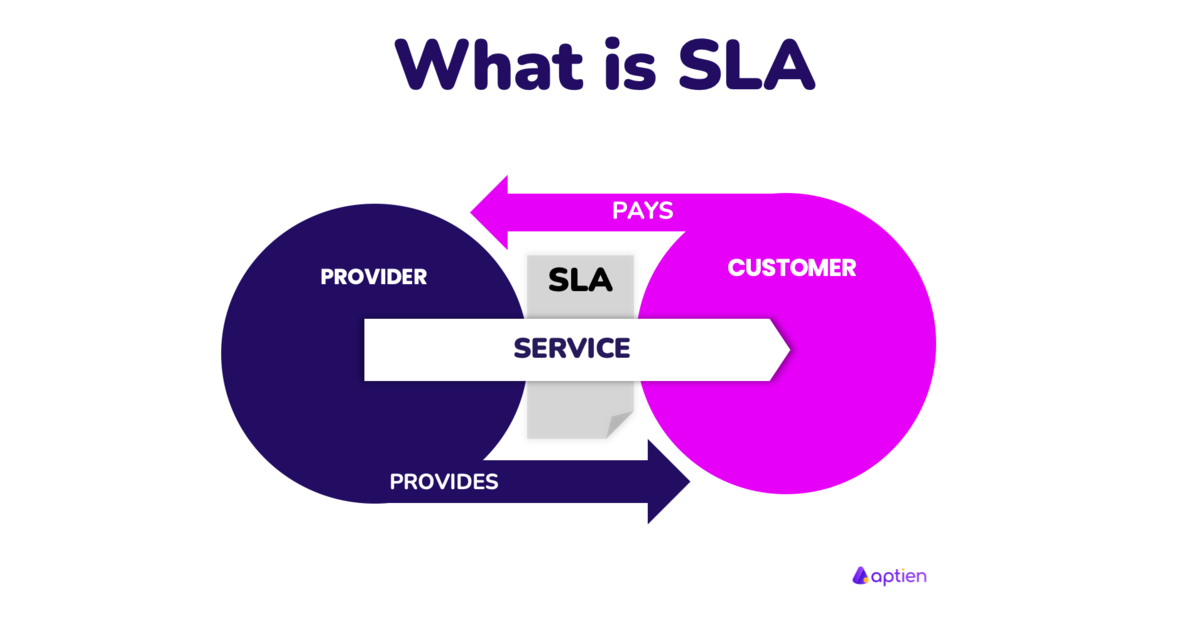
What is SLA Service Management Aptien
Vulnerability Management SLAs A Guide Part 1
What is SLA amp How Can it Benefit Your Business Development
What is SLA amp How Can it Benefit Your Business Development
Vulnerability timelines SLA Measurement and prioritization the how
Vulnerability timelines SLA Measurement and prioritization the how
Vulnerability timelines SLA Measurement and prioritization the how
What is SLA amp How Can it Benefit Your Business Development
What is SLA amp How Can it Benefit Your Business Development
Vulnerability timelines SLA Measurement and prioritization the how
Vulnerability timelines SLA Measurement and prioritization the how
Vulnerability timelines SLA Measurement and prioritization the how
Vulnerability timelines SLA Measurement and prioritization the how
Vulnerability timelines SLA Measurement and prioritization the how
Vulnerability timelines SLA Measurement and prioritization the how
Vulnerability timelines SLA Measurement and prioritization the how
Vulnerability timelines SLA Measurement and prioritization the how
Vulnerability timelines SLA Measurement and prioritization the how
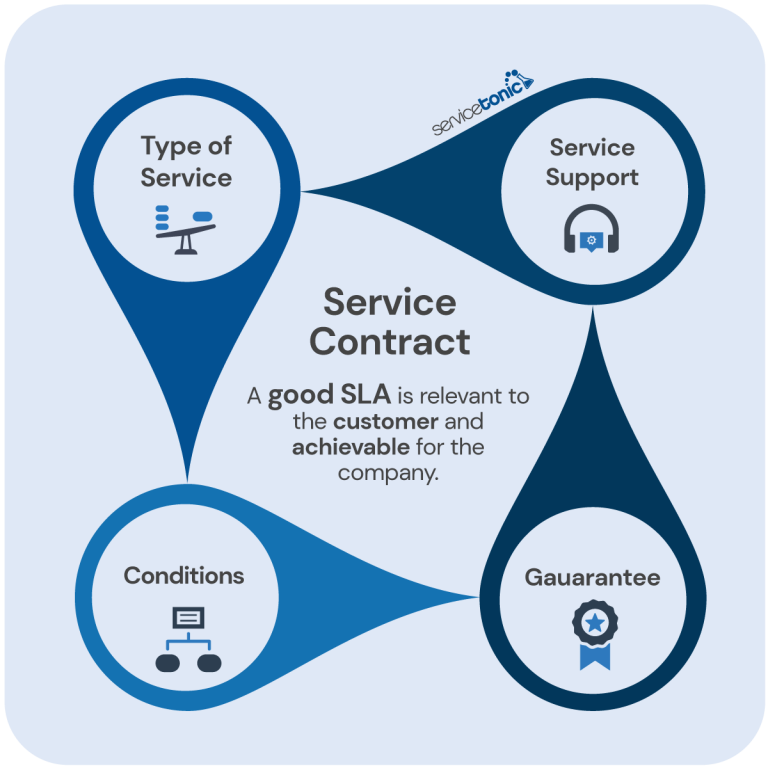
What is an SLA SLA definition and examples ServiceTonic
What is an SLA Definition Examples and Tips for Small Businesses
What is an SLA Definition Examples and Tips for Small Businesses
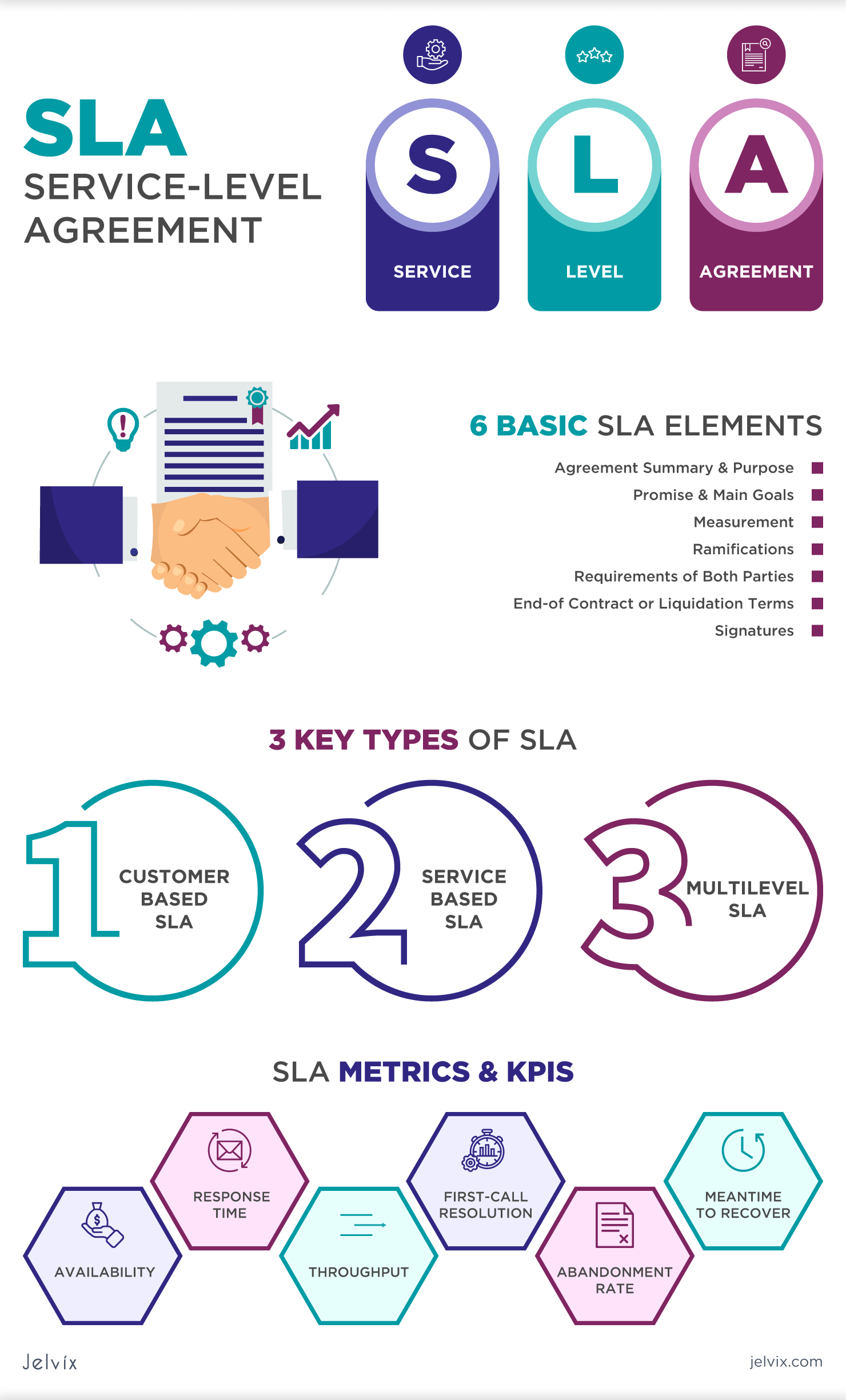
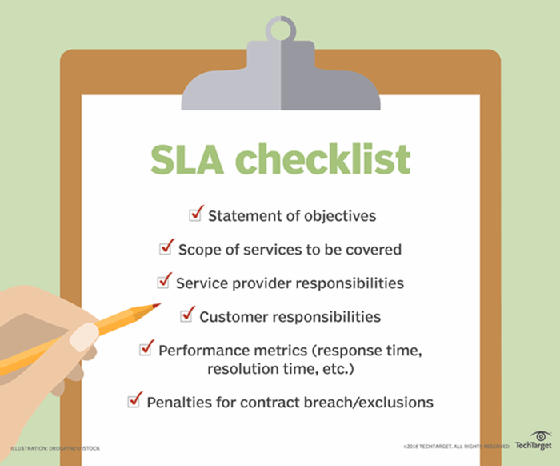
What is SLA Definition Types Components Metrics amp Steps
Service Level Agreement SLA for ServiceNow DxSherpa
Vulnerability timelines SLA Measurement and prioritization the how
What is an SLA Why are they important for your business Icertis
Are SLA Breaches Inevitable Hiplink
How to Manage SLA Risks and Contingencies Effectively
SLA Management Tips to Manage and Mitigate Risks
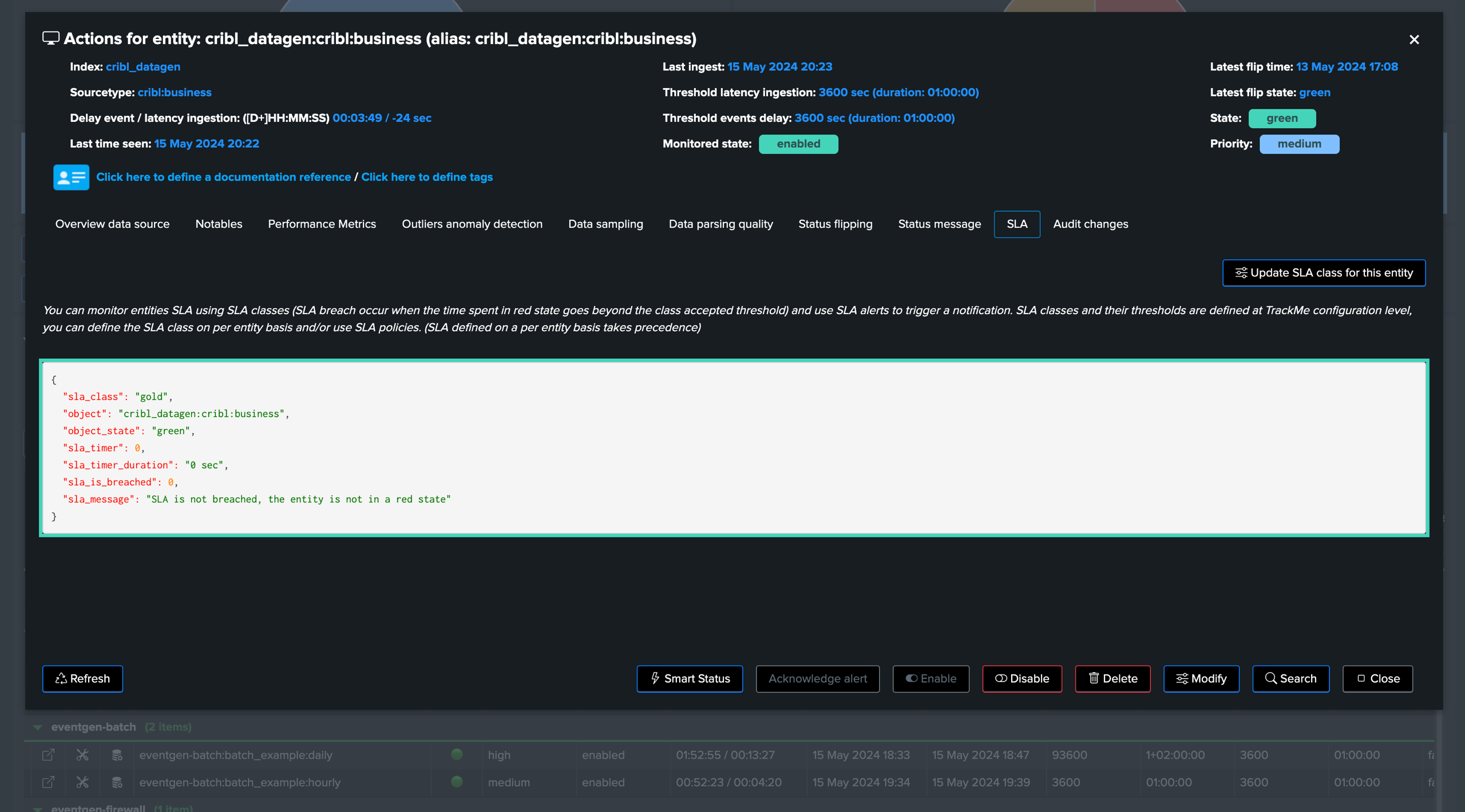
Using SLA alerting to build a 2 tier monitoring system TrackMe 2
4 Keys to Effective SLA Project Management Impero
What is SLA How to Handle SLA Breaches
What is SLA How to Handle SLA Breaches
Nucleus Blog How to Define Vulnerability Remediation SLAs
What is an SLA and Why is it important in Cloud Computing
Role of Service Level Agreements SLAs in Effective Outsourcing
What is SLA How to Handle SLA Breaches
What is SLA How to Handle SLA Breaches
Nucleus Blog How to Define Vulnerability Remediation SLAs
What is an SLA and Why is it important in Cloud Computing
Role of Service Level Agreements SLAs in Effective Outsourcing
How to set SLAs in Vulnerability Management Best Practices RankedRight
How to set SLAs in Vulnerability Management Best Practices RankedRight
What is sla how can it benefit your business development Artofit
Service Level Agreement SLA examples for IT support A guide
Using SLAs for Better Vulnerability Management amp Remediation Improving
Why SLA compliance should be top of mind for IT leaders TechTarget
Using SLAs for Better Vulnerability Management amp Remediation Improving
InsightVM SLAs Timely Vulnerability Remediation Made Easy Rapid7 Blog
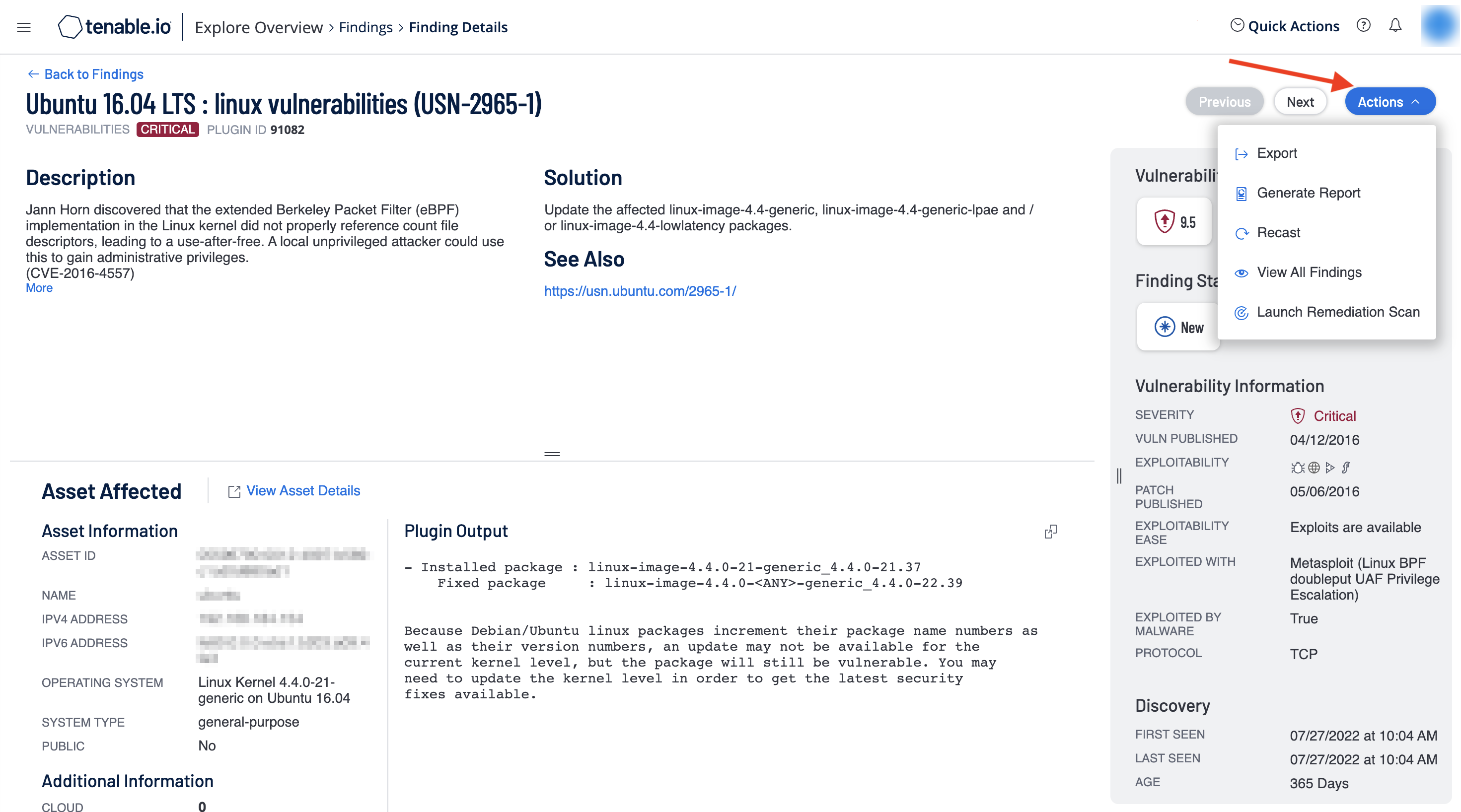
Part 1 An In Depth Look at the Latest Vulnerability Threat Landscape
Cover 97 of the vulnerability management process Medium
How to define Vulnerability Remediation SLAs YouTube
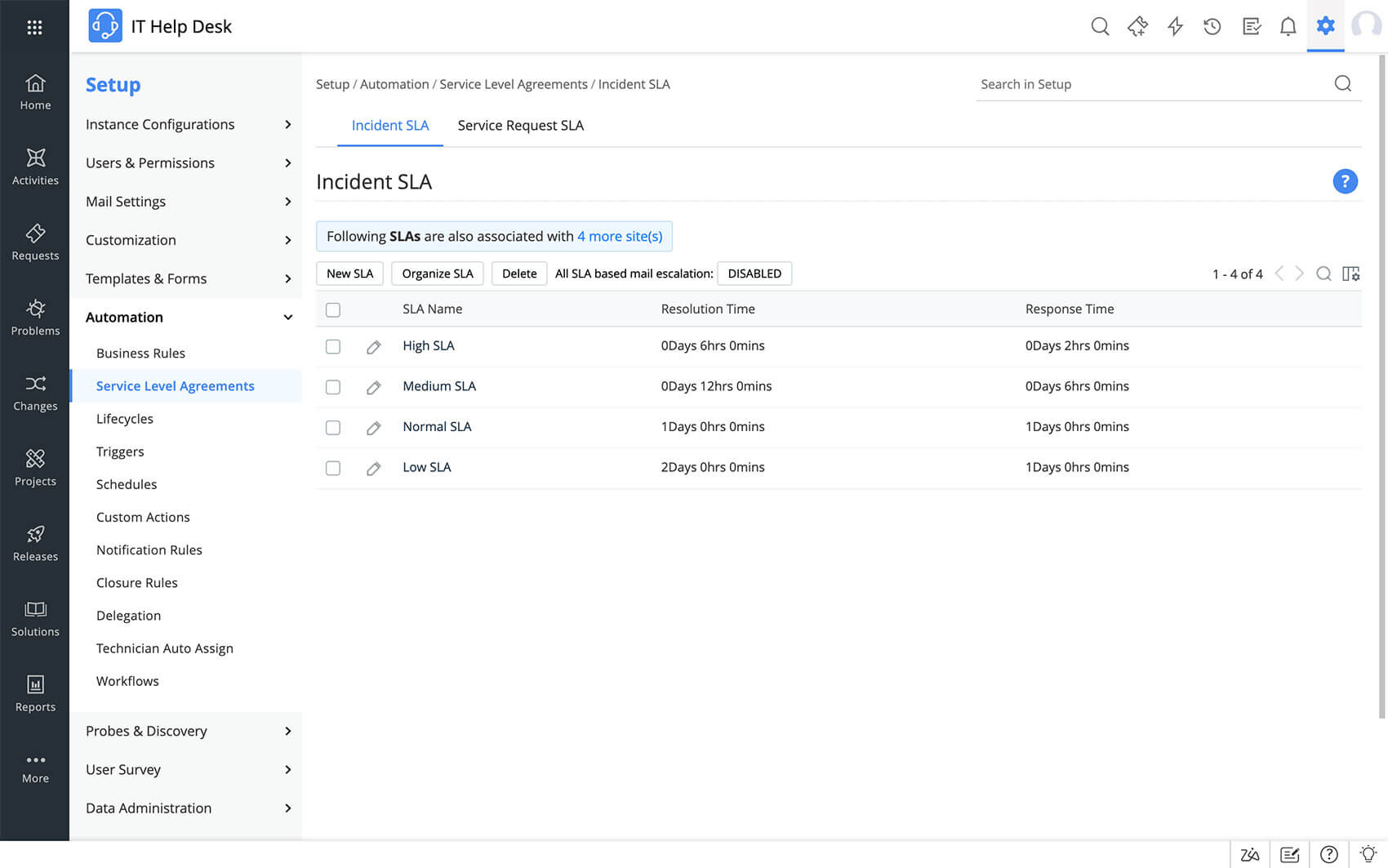
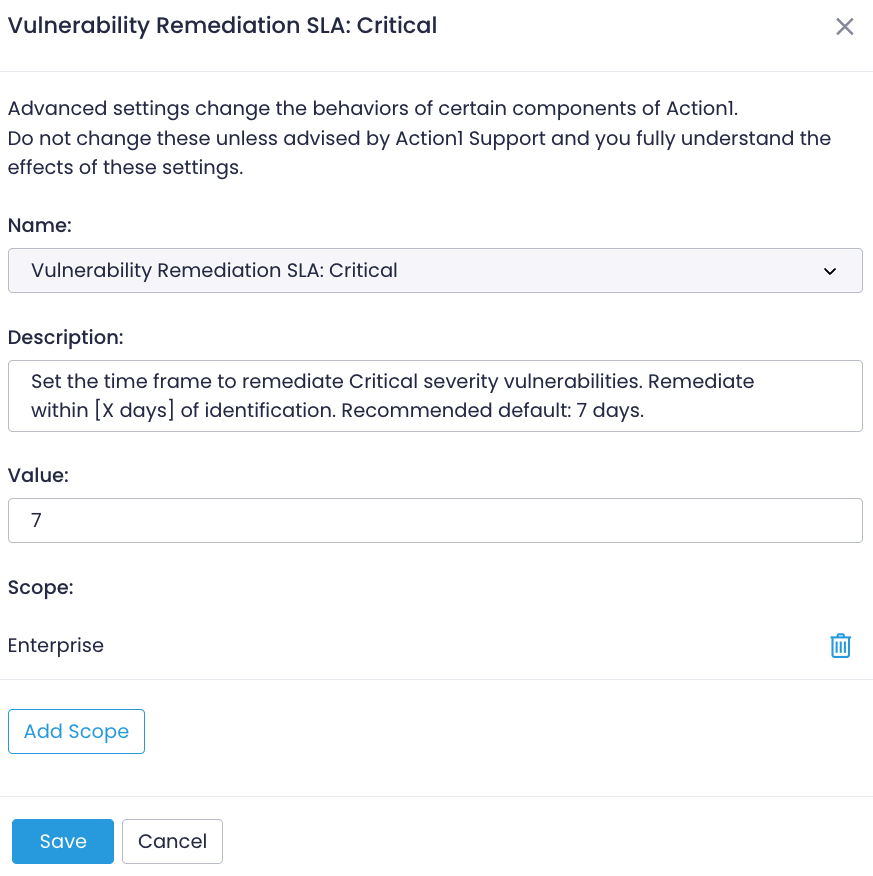
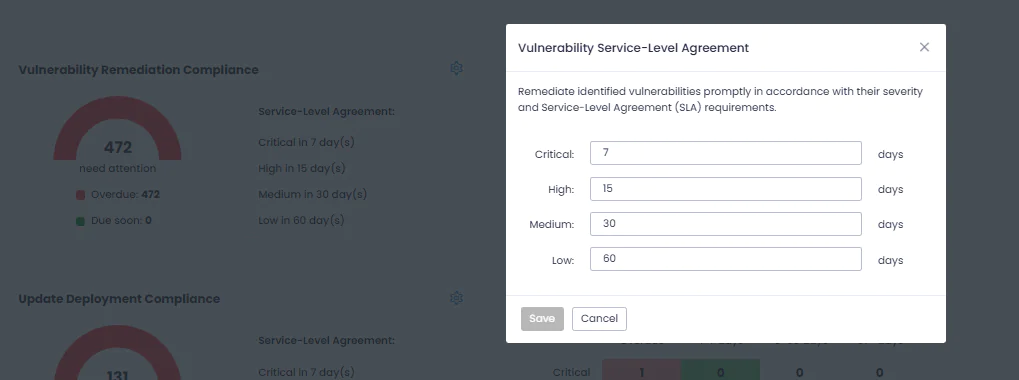
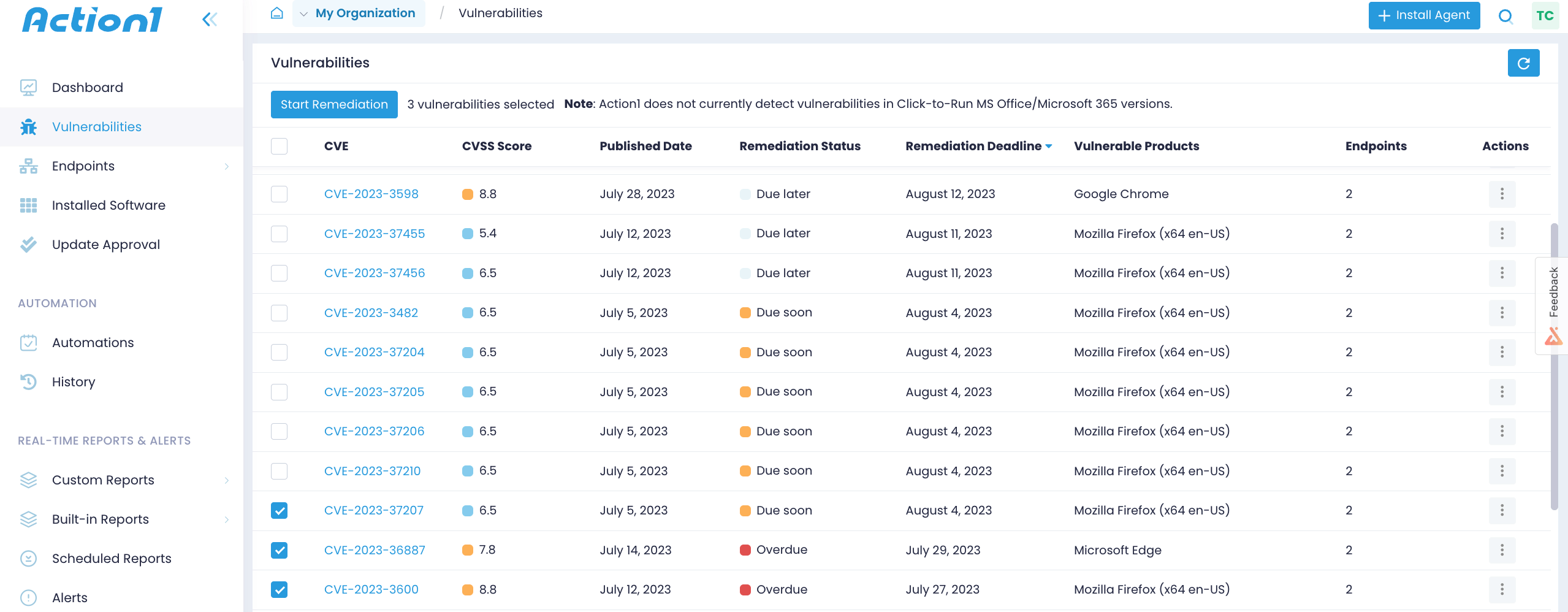
Configure SLAs Documentation Action1
Configure SLAs Documentation Action1
Configure SLAs Documentation Action1
Discover SLA breaches with our cutting edge technology Discover SLA
Discover SLA breaches with our cutting edge technology Discover SLA
What is SLA SLA best practices
Discover SLA breaches with our cutting edge technology Discover SLA
Discover SLA breaches with our cutting edge technology Discover SLA
Common SLA Cloud Operations Center Huawei Cloud
Setting Up Your Risk Based SLAs Kenna FAQ
Understanding SLAs in Cybersecurity
What Is Vulnerability Sla - The pictures related to be able to What Is Vulnerability Sla in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.