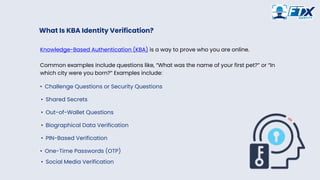
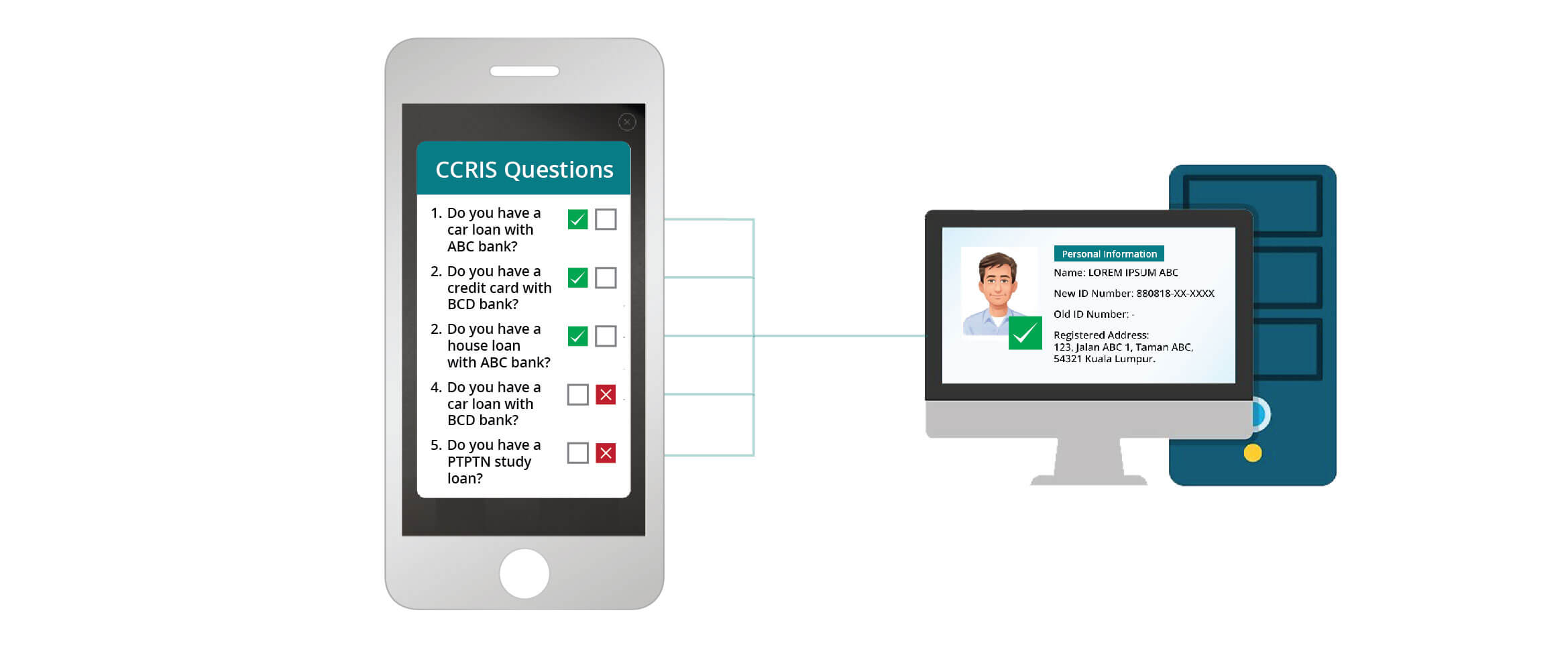
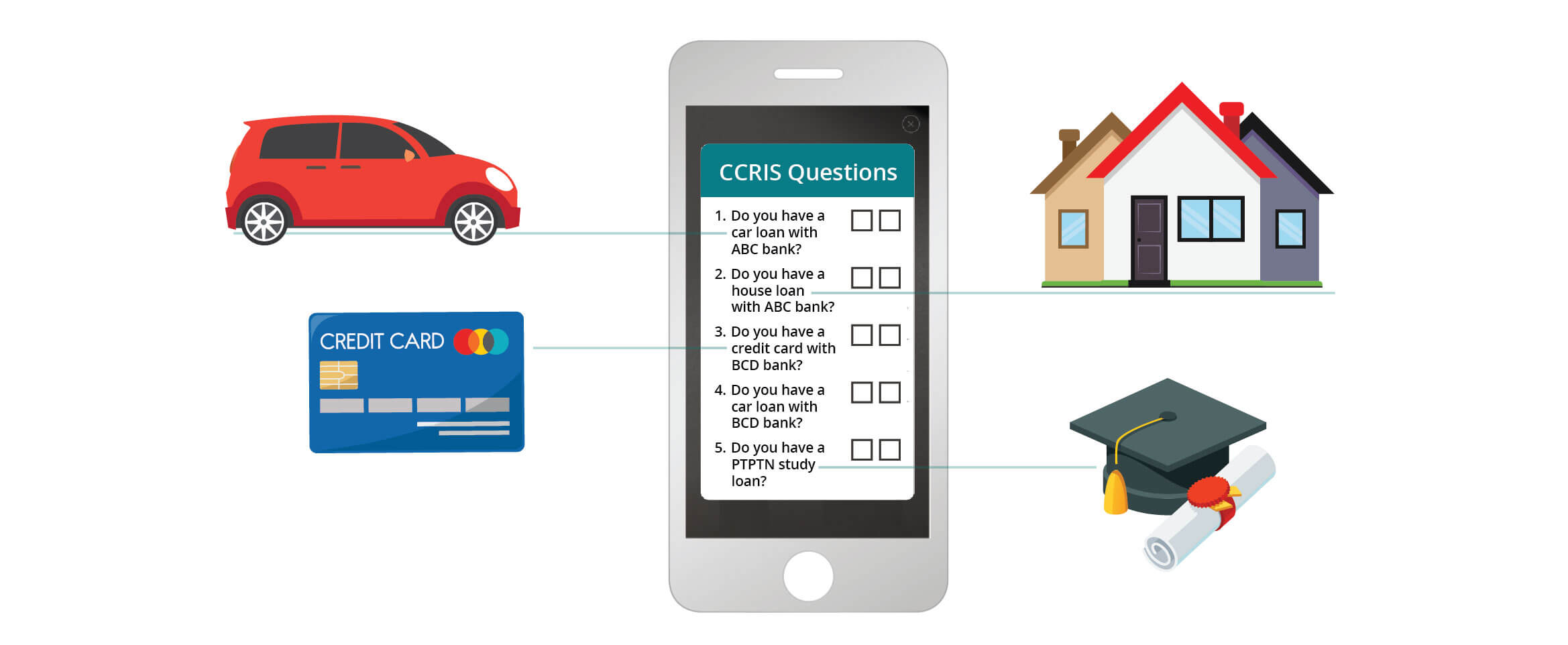
Knowledge-based authentication, commonly referred to as KBA, is a method of authentication which seeks to prove the identity of someone accessing a service Knowledge-based authentication (KBA) is an authentication method in which users are asked to answer at least one secret question. KBA is often used as a component in
Answering security questions based on personal information when you log in to an app or system is called knowledge-based authentication (KBA). While KBA is KBA, or Knowledge Based Authentication, is an established technique that uses information that only users should know to verify their identities. Despite its
Related Posts of What Is Knowledge Based Authentication :
Knowledge-based authentication, commonly referred to as KBA, is a method of authentication which seeks to prove the identity of someone accessing a service
Knowledge-based authentication (KBA) is an authentication method in which users are asked to answer at least one secret question. KBA is often used as a component in
Answering security questions based on personal information when you log in to an app or system is called knowledge-based authentication (KBA). While KBA is
KBA, or Knowledge Based Authentication, is an established technique that uses information that only users should know to verify their identities. Despite its
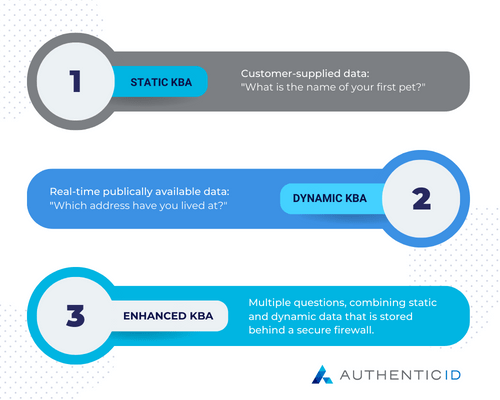
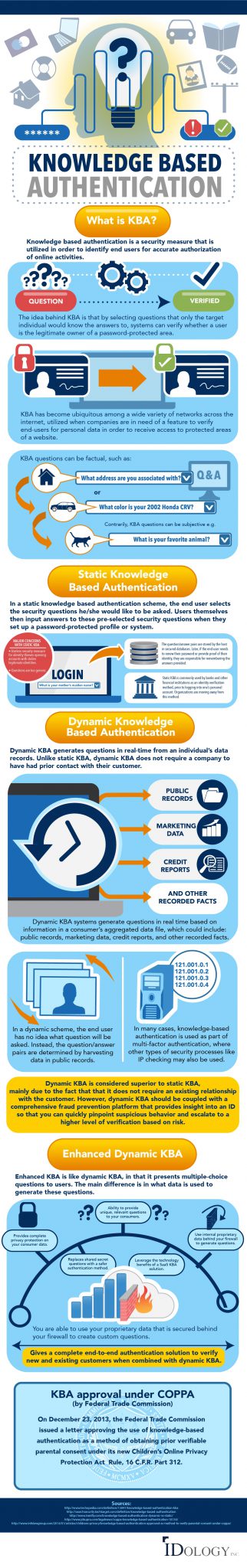
Knowledge-based authentication (KBA) is a security measure that verifies a user's identity by asking a series of questions that only the legitimate user should know. These
Knowledge Based Authentication KBA Powerful verification based on
What is Knowledge Based Authentication KBA AuthenticID
Knowledge Based Authentication The Difference between Static Dynamic
DocuSign Knowledge Based Authentication KBA
Identity Verification Dynamic KBA Knowledge Based Authentication
Turn Still relying on knowledge based authentication
Knowledge Based Authentication KBA Stavvy
Turn Still relying on knowledge based authentication
Comparing Static And Dynamic Knowledge Based Authentication
Classification of user authentication Knowledge based authentication
Knowledge based authentication with Zoho Sign
5 Best Knowledge Based Authentication KBA Alternatives PDF
5 Knowledge Based Authentication Alternatives for Better Security
5 Knowledge Based Authentication Alternatives for Better Security
The Crucial Role of Knowledge Based Authentication in B2B Transactions
It s Time to Replace Knowledge Based Authentication
PDF Developing User Authentication by Knowledge Based Authentication
Understanding Knowledge Based Authentication and Its Mechanics
Knowledge based Authentication Compliance and Tax Season
Is the Internet killing Knowledge Based Authentication
5 Knowledge Based Authentication Alternatives for Better Security
5 Knowledge Based Authentication Alternatives for Better Security
The Crucial Role of Knowledge Based Authentication in B2B Transactions
It s Time to Replace Knowledge Based Authentication
PDF Developing User Authentication by Knowledge Based Authentication
Infographic What is KBA Knowledge Based Authentication Explained
Understanding Knowledge Based Authentication and Its Mechanics
Knowledge based Authentication Compliance and Tax Season
Is the Internet killing Knowledge Based Authentication
When creating Knowledge Based Authentication KBA answers put
5 Best Alternatives to Knowledge Based Authentication for Enhancing
PPT Enhancing Security with Knowledge Based Authentication Provider
Knowledge Based Authentication or KBA Remote Online Notary
Episode 245 How AI is remaking knowledge based authentication
An end to end guide on knowledge based authentication
CTOS Identity Verification helps you to protect your customers
CTOS Identity Verification helps you to protect your customers
Key based Authentication Method A Prominent Alternative
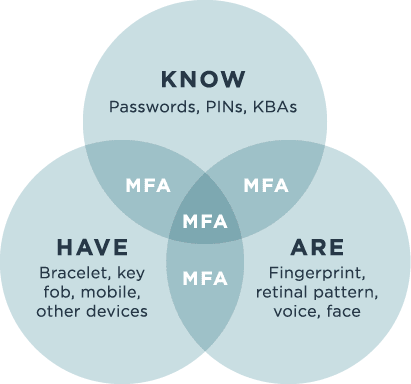
Biometric Something you are This is an inherited trait and confirmed
Token Based Authentication For Security and User Experience
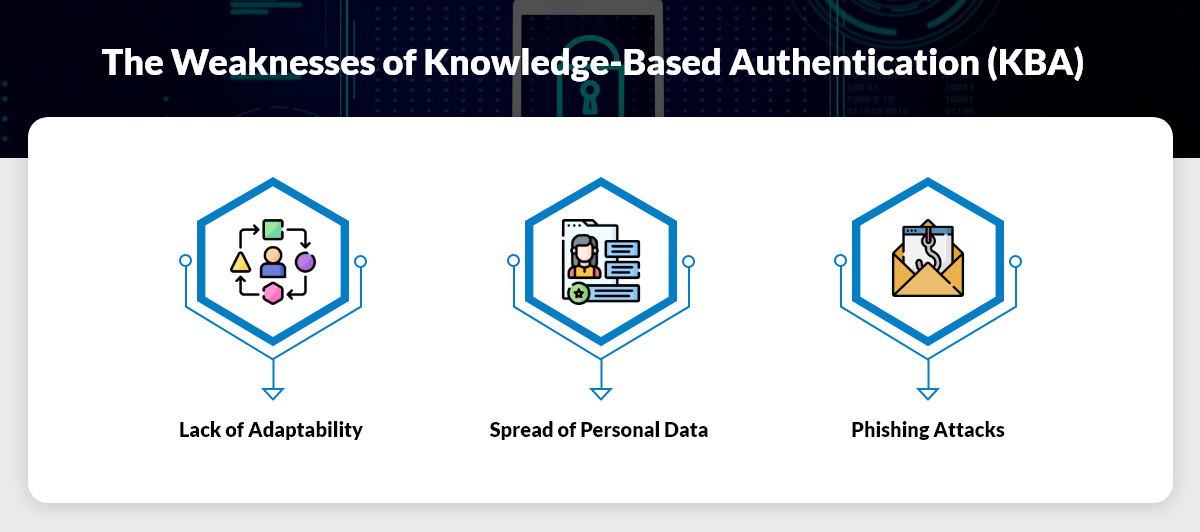
Everybody Knows How Knowledge Based Authentication Died
Pros and Cons of Knowledge Based Authentication for E Signatures
Knowledge Based Authentication a Thing of Past Shufti
Knowledge Based Authentication is Dead We Need a New Multidimensional
Knowledge Based Authentication is Dead We Need a New Multidimensional
Knowledge Based Authentication is Dead We Need a New Multidimensional
Knowledge Based Authentication is Dead We Need a New Multidimensional
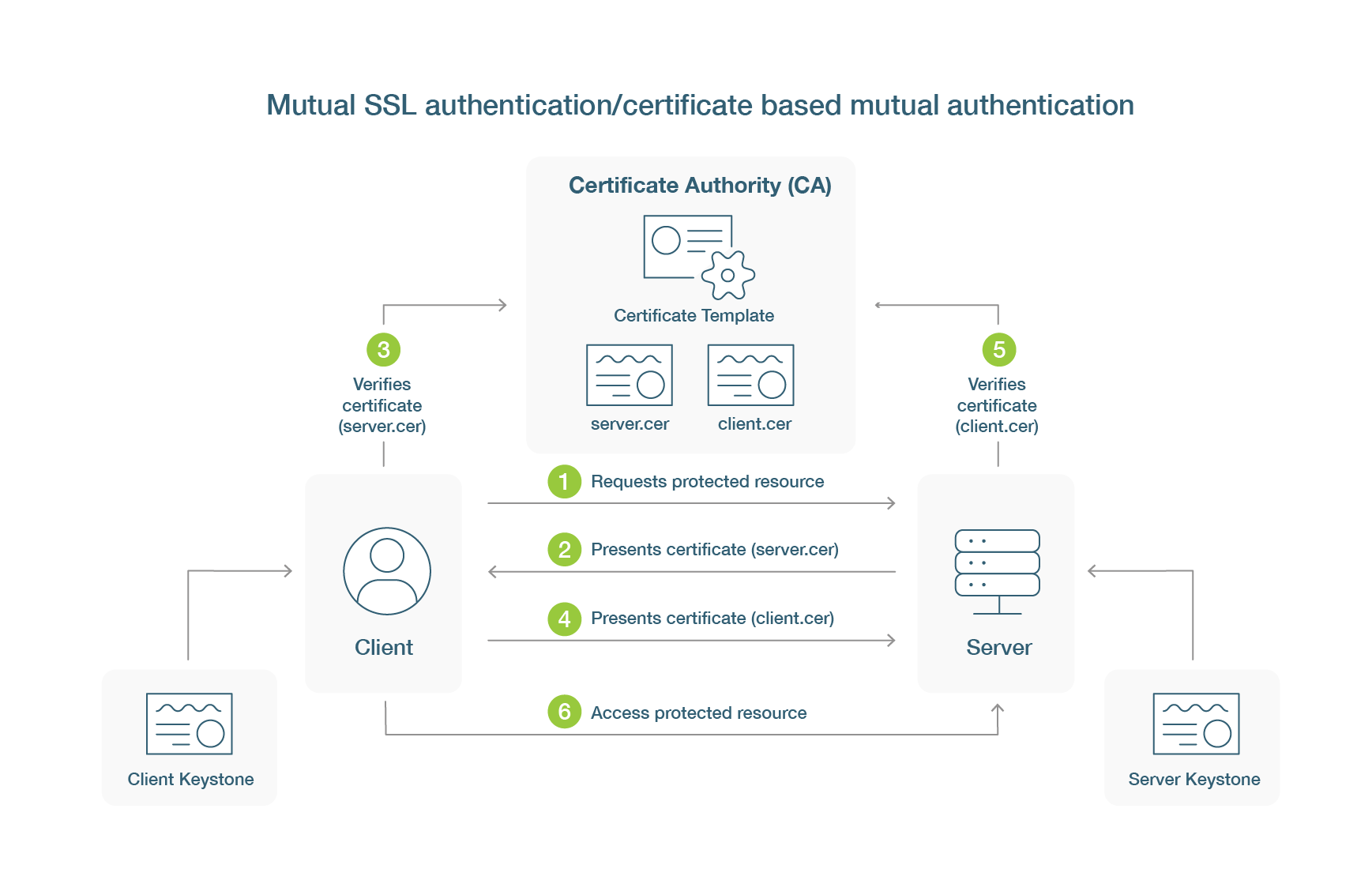
Where Does Certificate Based Authentication Fit Into Modern
Knowledge Based Authentication is Dead We Need a New Multidimensional
Knowledge Based Authentication is Dead We Need a New Multidimensional
Where Does Certificate Based Authentication Fit Into Modern
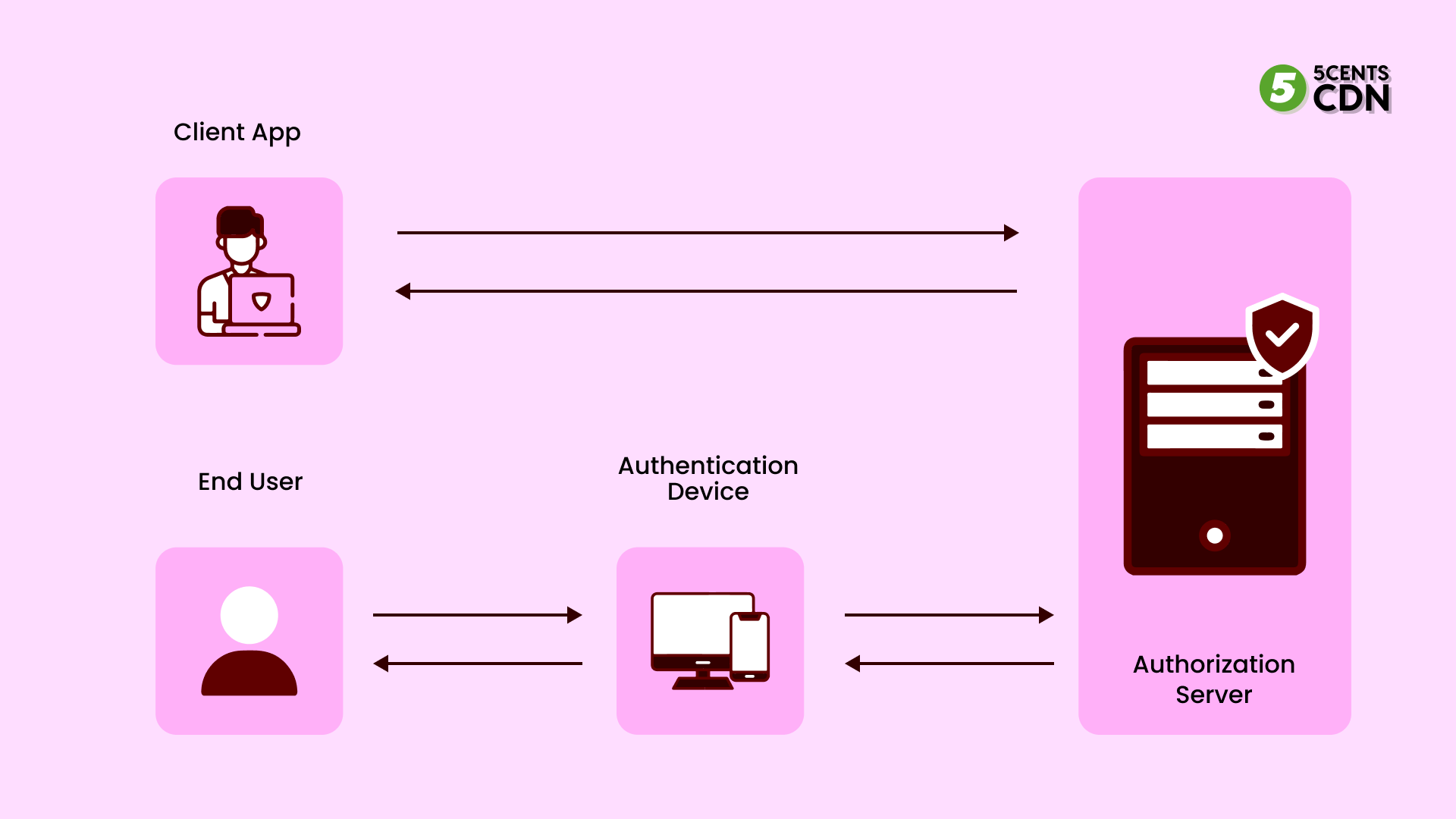
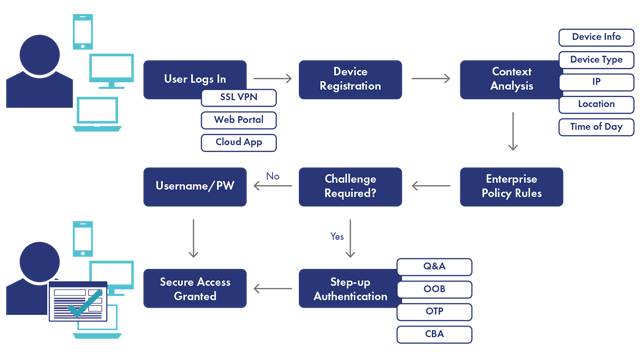
Context Based Authentication Solutions
Figure 3 from Zero Knowledge based Authentication for Internet of
Knowledge Based Verification KBV CyberHoot
Figure 1 from Knowledge based Authentication Techniques and Challenges
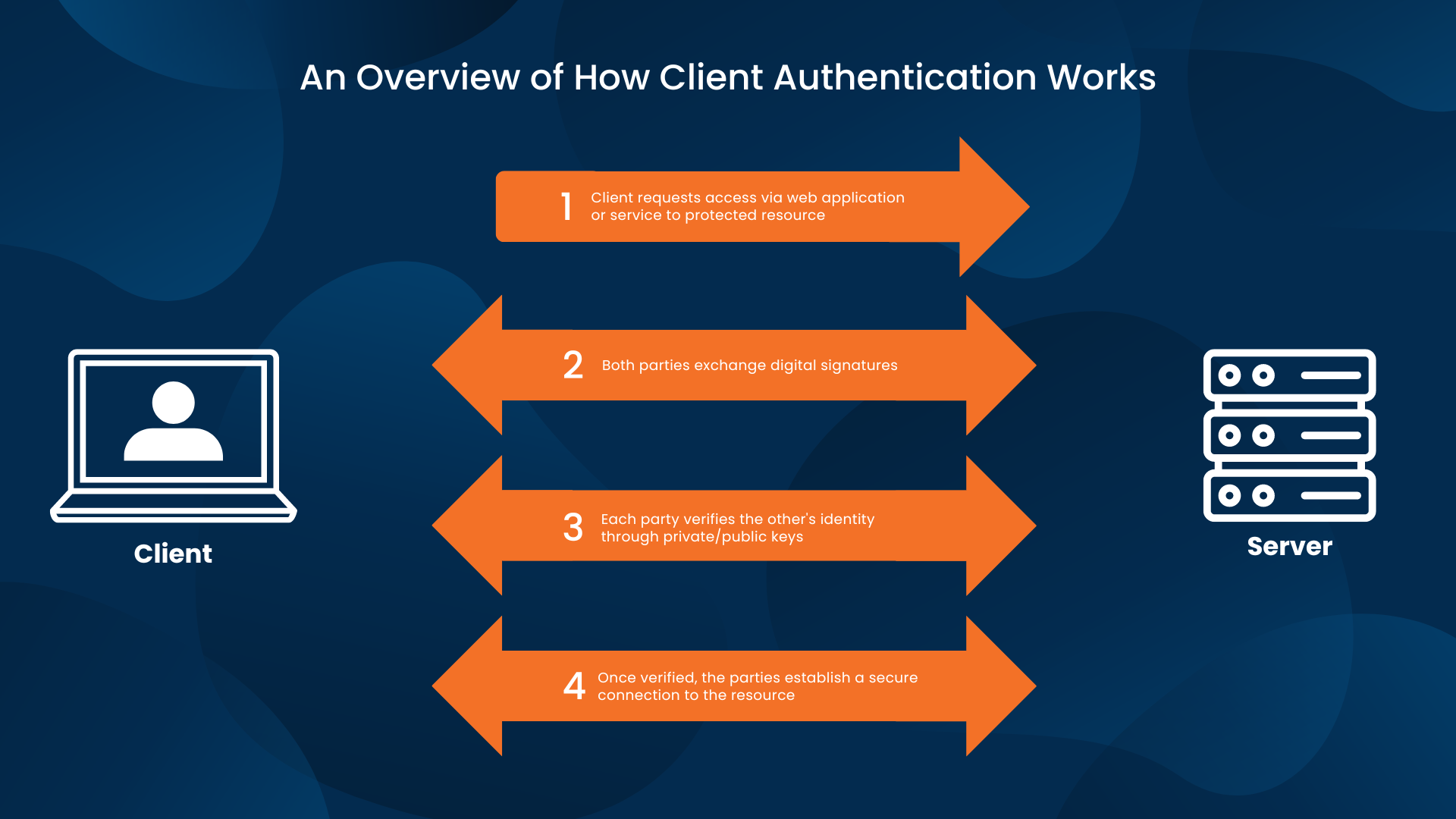
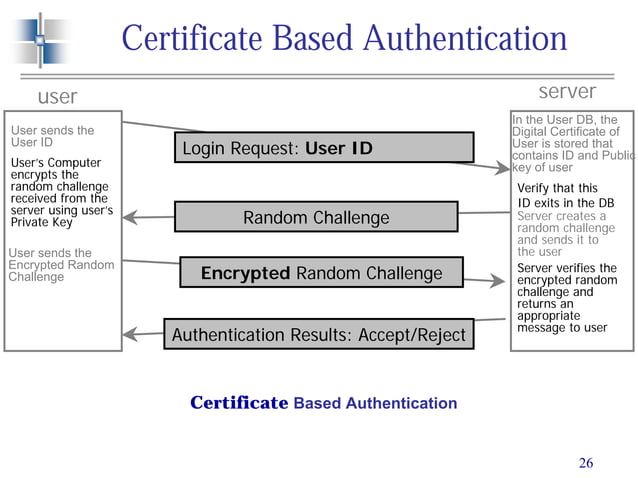
What is Certificate Based Authentication Yubico
What is Certificate based Authentication GlobalSign
SOLUTION Analysis of knowledge based authentication system using
PDF Security and Usability in Knowledge based User Authentication A
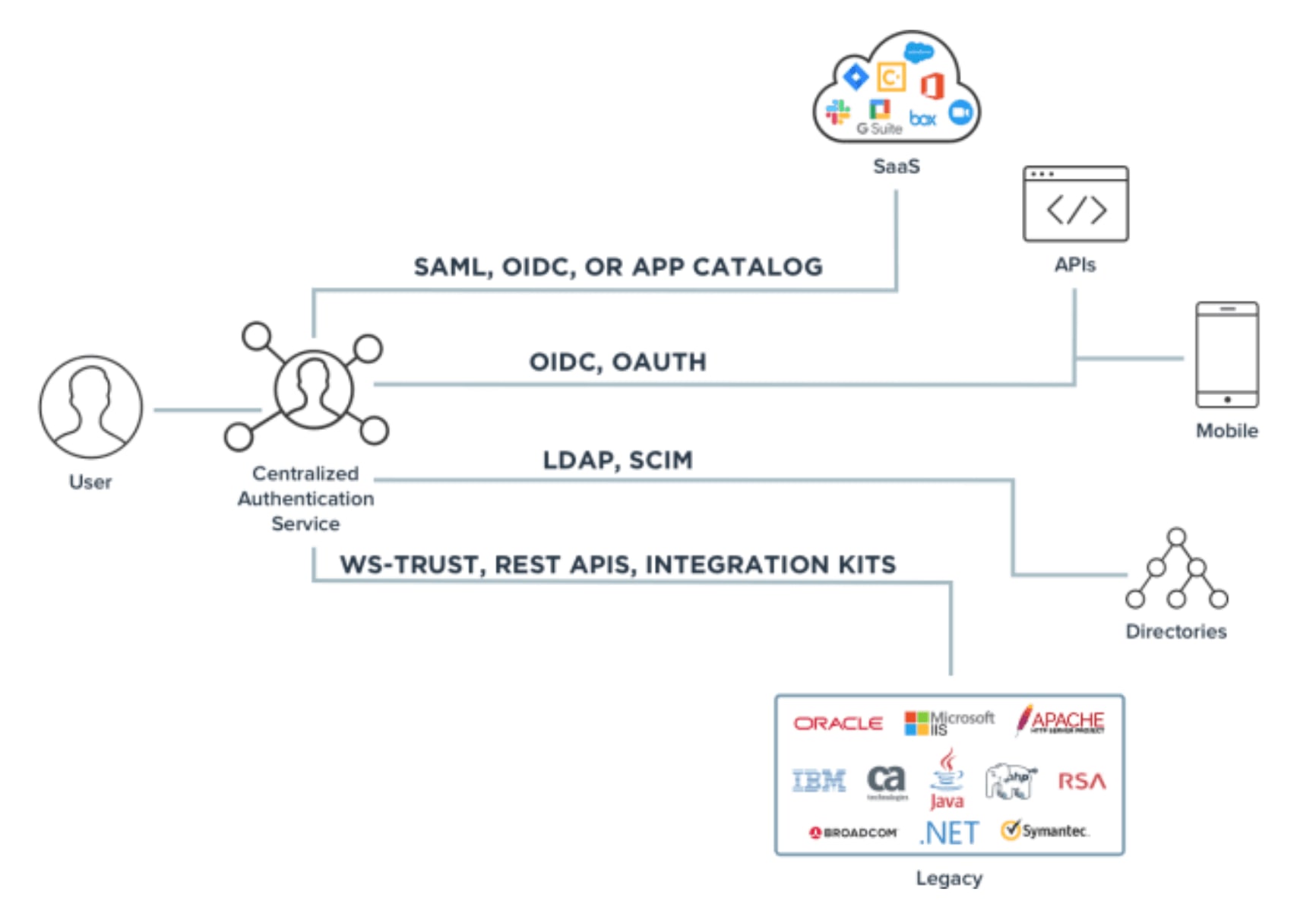
Authentication techniques
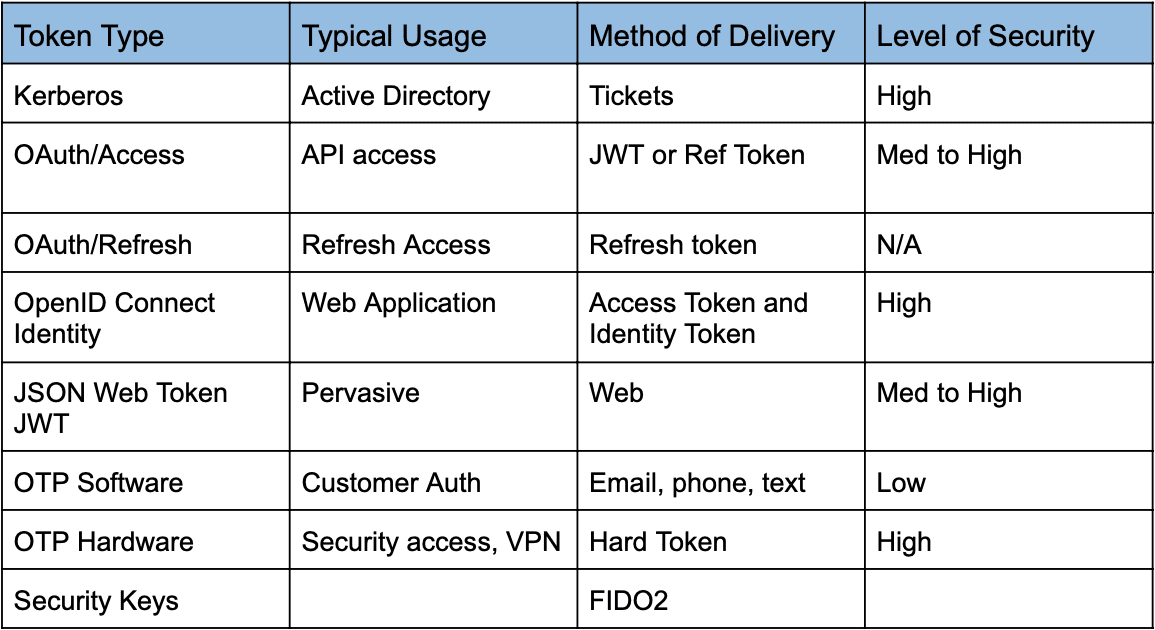
What is Token based Authentication for Web APIs
How token based authentication works graphic
Knowledge based Authentication Alternative in iGaming
Token based authentication In the modern digital era the way web
Token Based Authentication What Is It and How It Works AppRiver
KBA Entenda o que 233 o knowledge based authentication
Best Practices for Authentication in Web Applications KAISPE
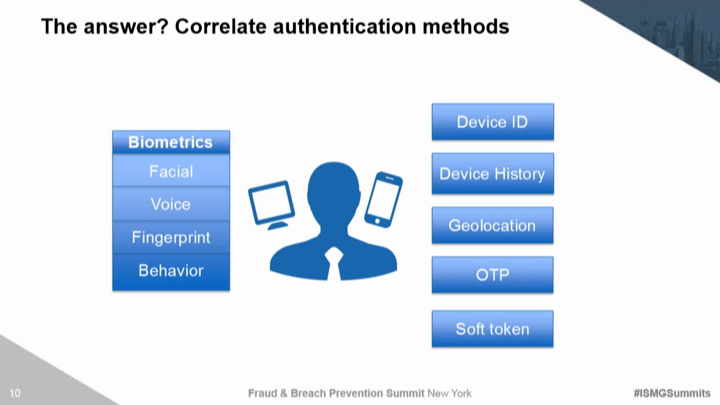
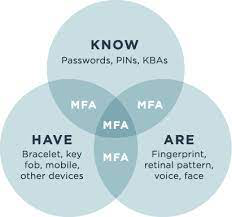
Types of Authentication Methods Optimal IdM
Adobe Acrobat Sign Identity Authentication Methods
What s the Best Authentication Method Analysis
PPT Authentication Mechanisms PowerPoint Presentation free download
PPT Authentication Mechanisms PowerPoint Presentation free download
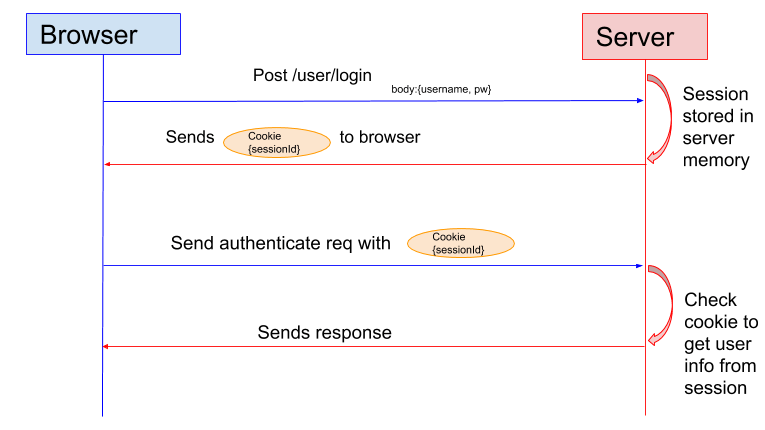
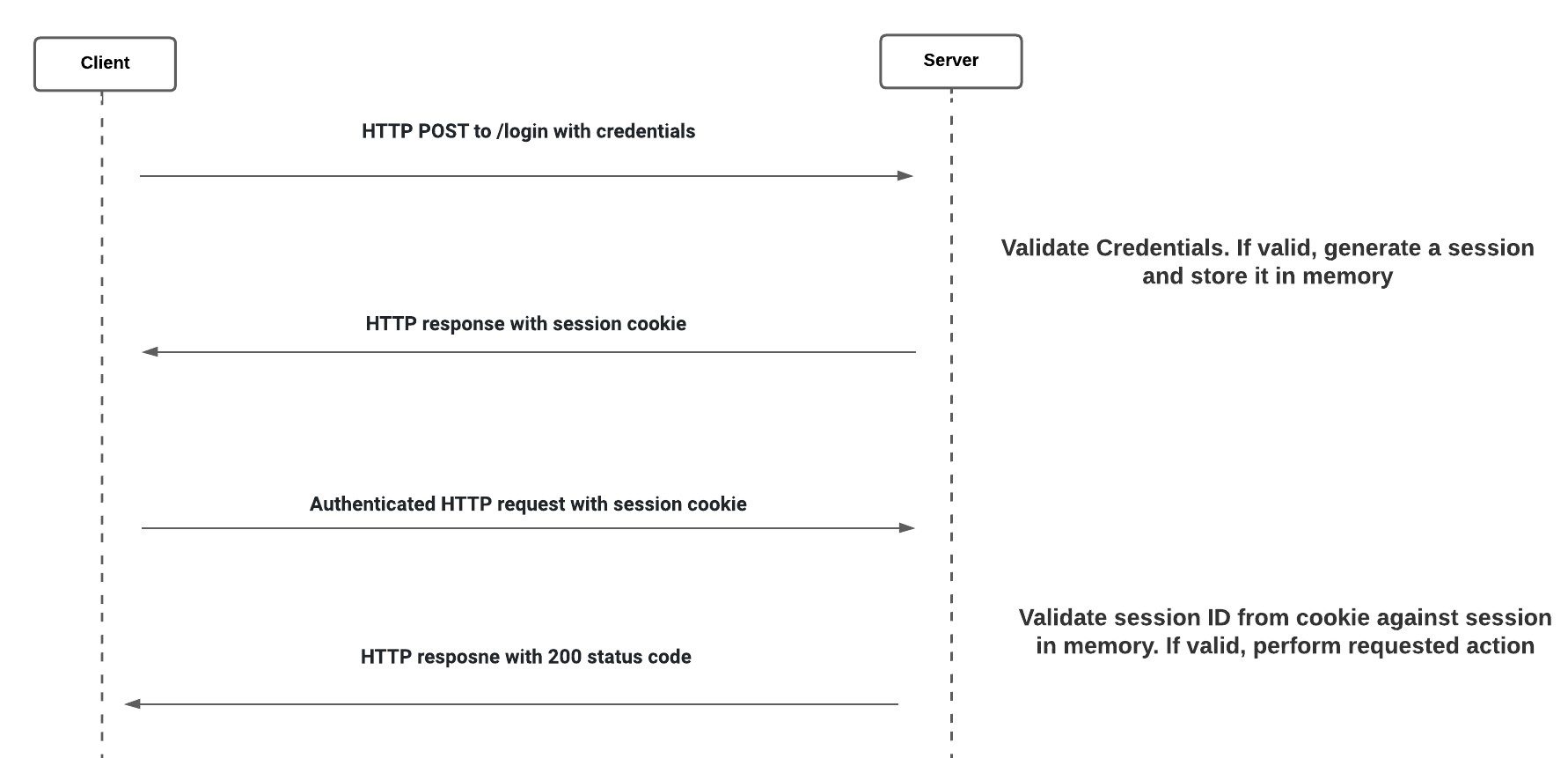
Knowledge based authentication
Comprehensive Guide to User Authentication Everything you should know
What is authentication What is authentication Authentication is the
What is Authentication What is Authentication The process of
What Is Knowledge Based Authentication - The pictures related to be able to What Is Knowledge Based Authentication in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.