A Vulnerability Scan of Your External IP Addresses with a Detailed
A complete guide to network vulnerability assessment
Network Vulnerability IV NETWORK VULNERABILITY There are many
This F5 BIG IP Vulnerability makes it easier for Ransomware to encrypt
IPV6 Vulnerability Surface
Unpatched DNS Vulnerability Affects Many IoT Products
Internet protocol version 6 vulnerability classes 185 179 Download
Intellectual Property Leakage Prevention Zero Trust Security
Strategies for Detecting and Preventing IP Abuse
Components of vulnerability according to the IPCC a and UNISDR b
IP Address What Is Types and How Does it Work Easily Explained
Understanding IP Abuse amp 4 Effect of IP Abuse VCCLHosting
IP Basics My business is a victim of IP Crime Knowledge Library
Protect against IP threats Raconteur
The HTTP 2 Fast Reset Attack Vulnerability What You Need To Know
3 Vulnerabilities Found on AvertX IP Cameras
The HTTP 2 Fast Reset Attack Vulnerability What You Need To Know
3 Vulnerabilities Found on AvertX IP Cameras
IP Vulnerabilities and Threats 187 CCNA 200 301
Pros and cons of external IPs Kaspersky official blog
PPT TCP IP Vulnerabilities PowerPoint Presentation free download
PPT TCP IP Vulnerabilities PowerPoint Presentation free download
3 Key IP Protection Issues That The World Is Currently Facing
New F5 BIG IP Vulnerabilities Exploited In The Wild Gridinsoft Blog
What are the Different Types of IP Address PyNet Labs
PPT TCP IP Vulnerabilities PowerPoint Presentation free download
Presentation On TCP IP Vulnerabilities PDF Transmission Control
Impact of IP Vulnerabilities The Ultimate goal for CCNA Cisco
Impact of IP Vulnerabilities The Ultimate goal for CCNA Cisco
Identifying and investigating malicious IP addresses and domains
The most threatening IP production risks Download Scientific Diagram
TCP IP stack vulnerabilities threaten IoT devices Network World
Is My IP Address a Threat to My Online and Offline Privacy
Is My IP Address a Threat to My Online and Offline Privacy
Is My IP Address a Threat to My Online and Offline Privacy
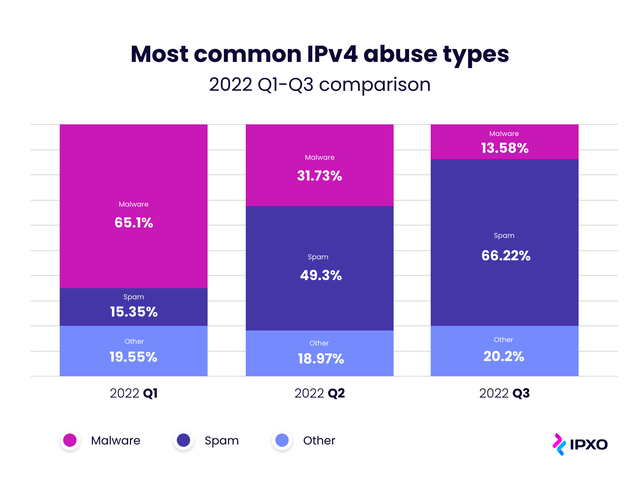
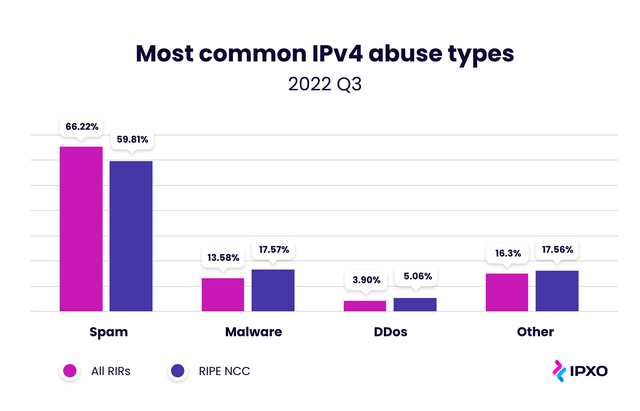
Facing and mitigating IP address abuse in IPv4 transfer and lease
Facing and mitigating IP address abuse in IPv4 transfer and lease
7 TCP IP vulnerabilities and how to prevent them TechTarget
Machine IP addresses and vulnerabilities Download Table
The Pentagon reportedly gave a small company control of its IP
Vulnerabilities in IP Protocols PPT
A vulnerabilities assessment for your IP addresses Upwork
Fighting IP abuse Tips and Resources for Reporting Incidents
7 TCP IP vulnerabilities and how to prevent them TechTarget
TCP IP stack vulnerabilities threaten IoT devices ThreatsHub
Machine IP addresses and vulnerabilities Download Table
The Pentagon reportedly gave a small company control of its IP
Vulnerabilities in IP Protocols PPT
A vulnerabilities assessment for your IP addresses Upwork
Fighting IP abuse Tips and Resources for Reporting Incidents
Hidden Threats of IP Addresses Exposure and Protection Telegraph
Your IP is Under Attack Learn How to Protect It From Every Angle Zix
What Are The Cybersecurity Vulnerabilities Of IP Based Systems
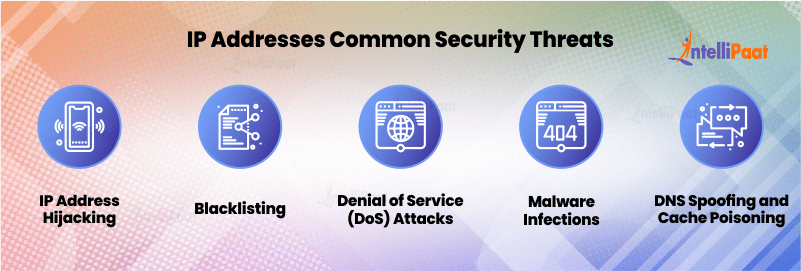
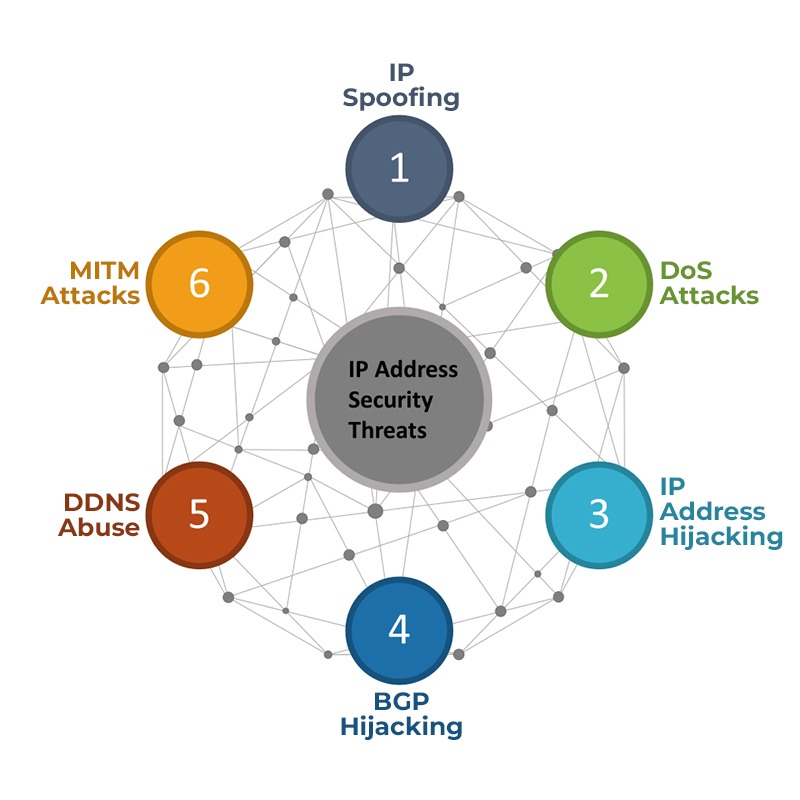
IP address security threats IP address security threats
Understanding the Basics of IP Addresses
7 TCP IP vulnerabilities and how to prevent them pdf PDF Host
A DEEP DIVE INTO DIFFERENT TYPES OF IP VIOLATIONS ON AMAZON by
Understanding Vulnerabilities in the TCP IP Model Part 1 Application
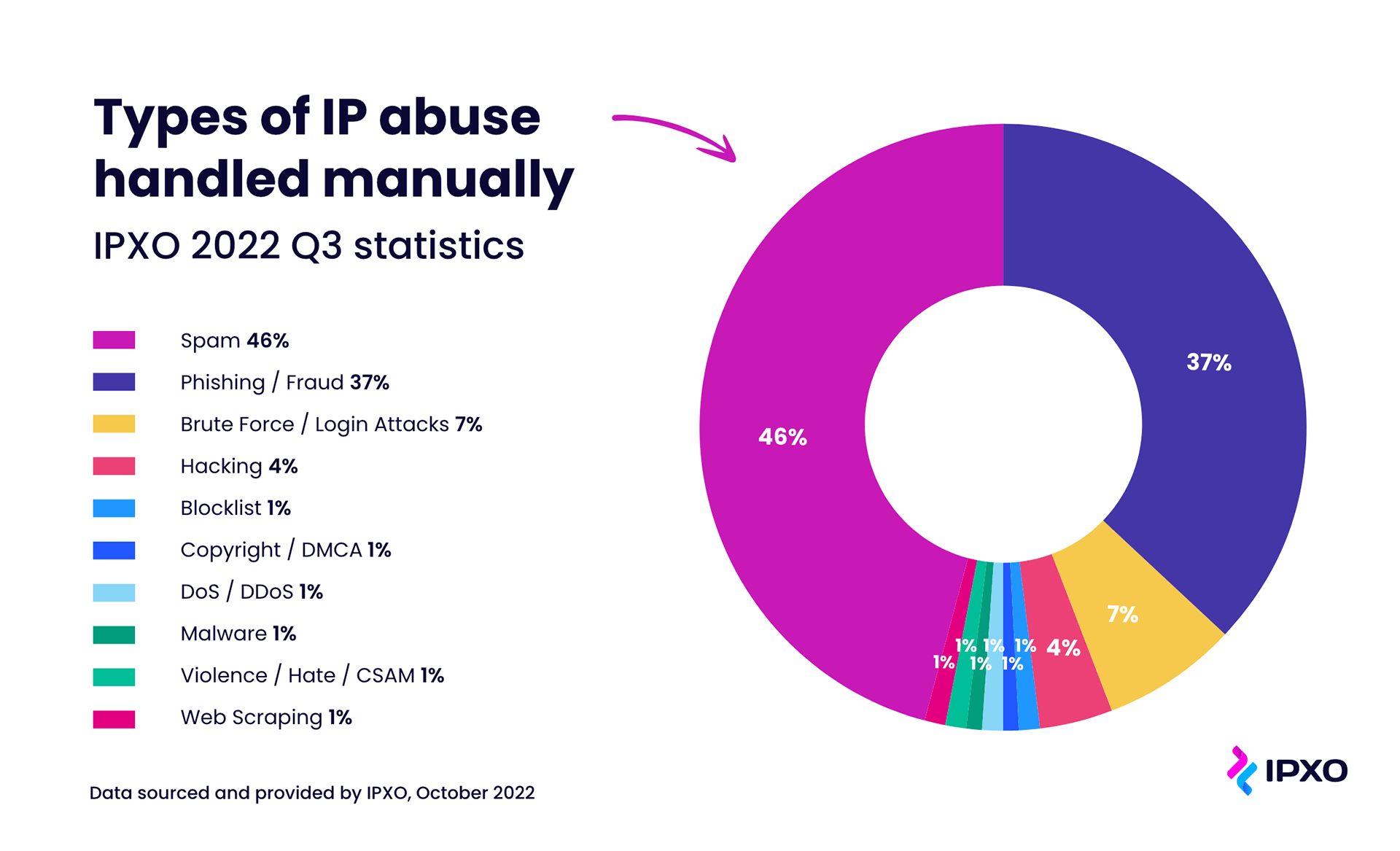
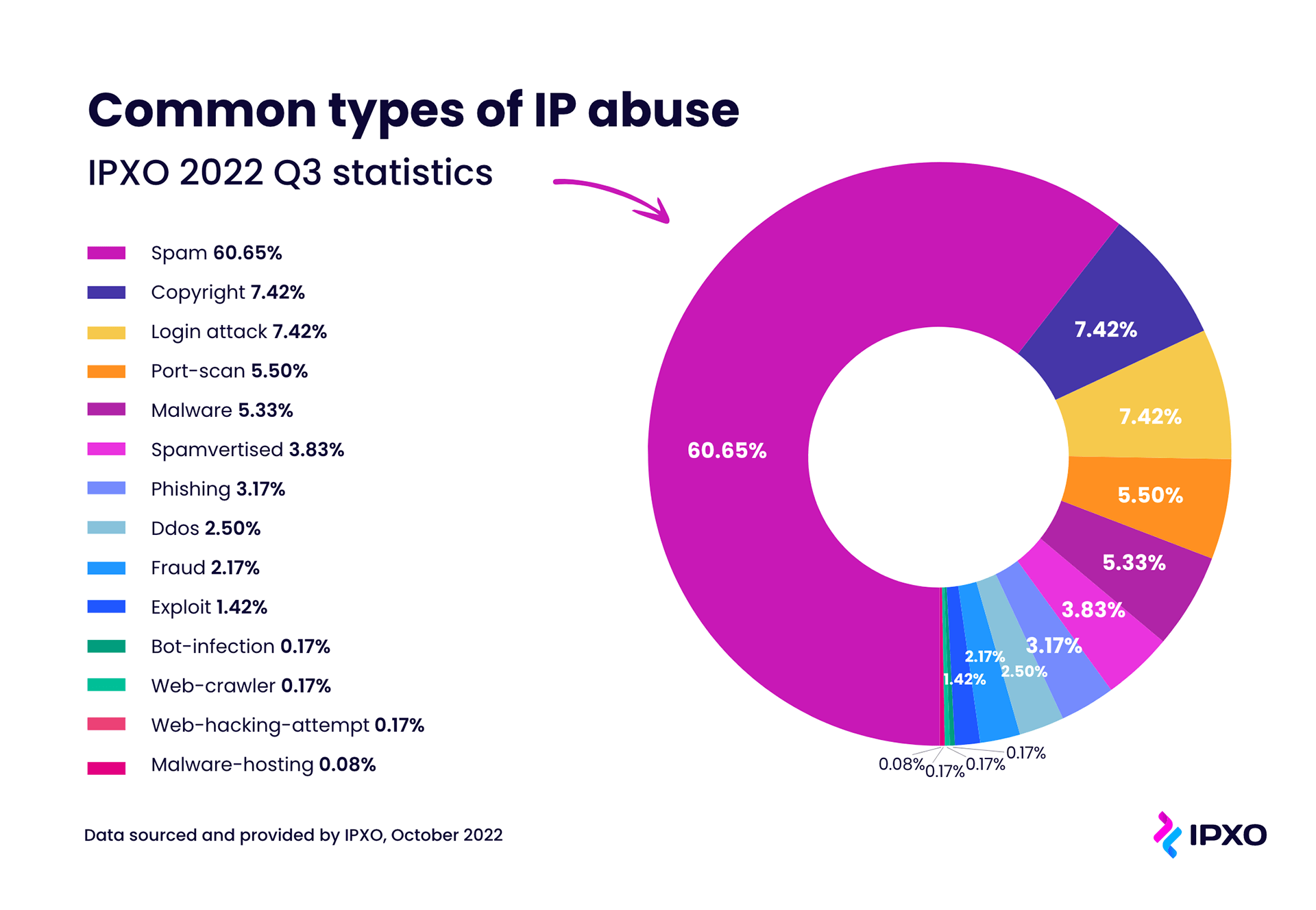
Top 3 Types of IP Address Abuse That Threaten IPv4 Resource Holders
Top 3 Types of IP Address Abuse That Threaten IPv4 Resource Holders
TCP IP Vulnerability Cryptography and System Security YouTube
The History of DNS Vulnerabilities and the Cloud
Severe vulnerabilities discovered in HTTP 2 protocol ZDNET
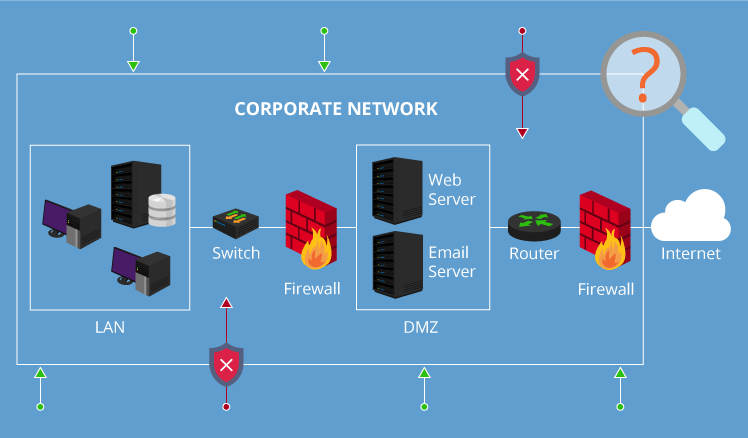
Securing information systems ppt download
Attacking IPv4 and IPv6 Vulnerabilities
Discovering and Resolving IP Address Vulnerabilities A Guide to
Chapter 6 IP Security ppt download
Securing Information Systems ppt download
Unveiling inherent vulnerabilities in VPN protocols risks and
Top Five Attacking IPs This Month Their Locations May Not Be Where You
Security Ad Hoc Report Draft ppt download
What Is Ip Vulnerability - The pictures related to be able to What Is Ip Vulnerability in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.




































:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/8792129/acastro_170621_1777_0008.jpg)