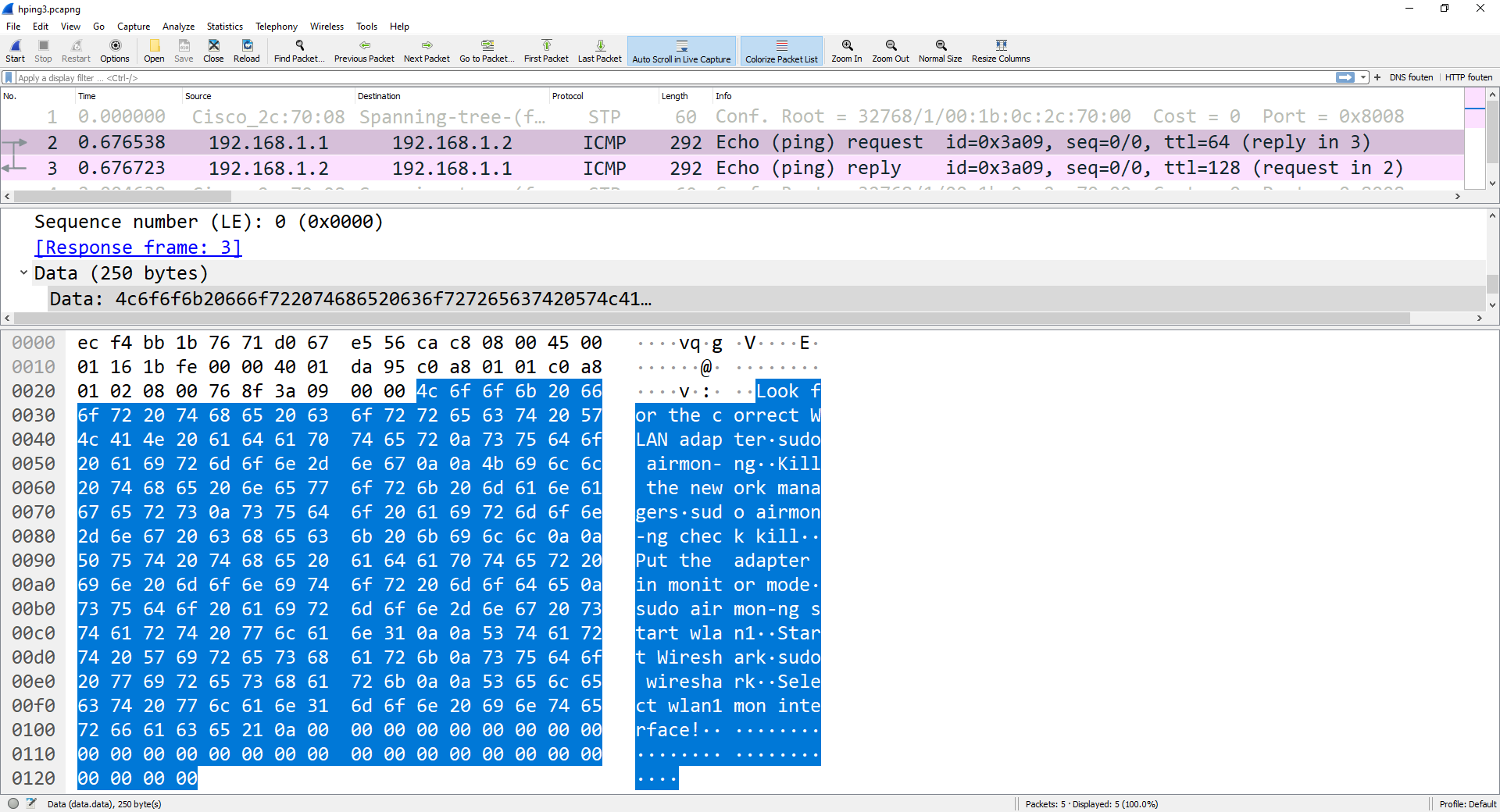
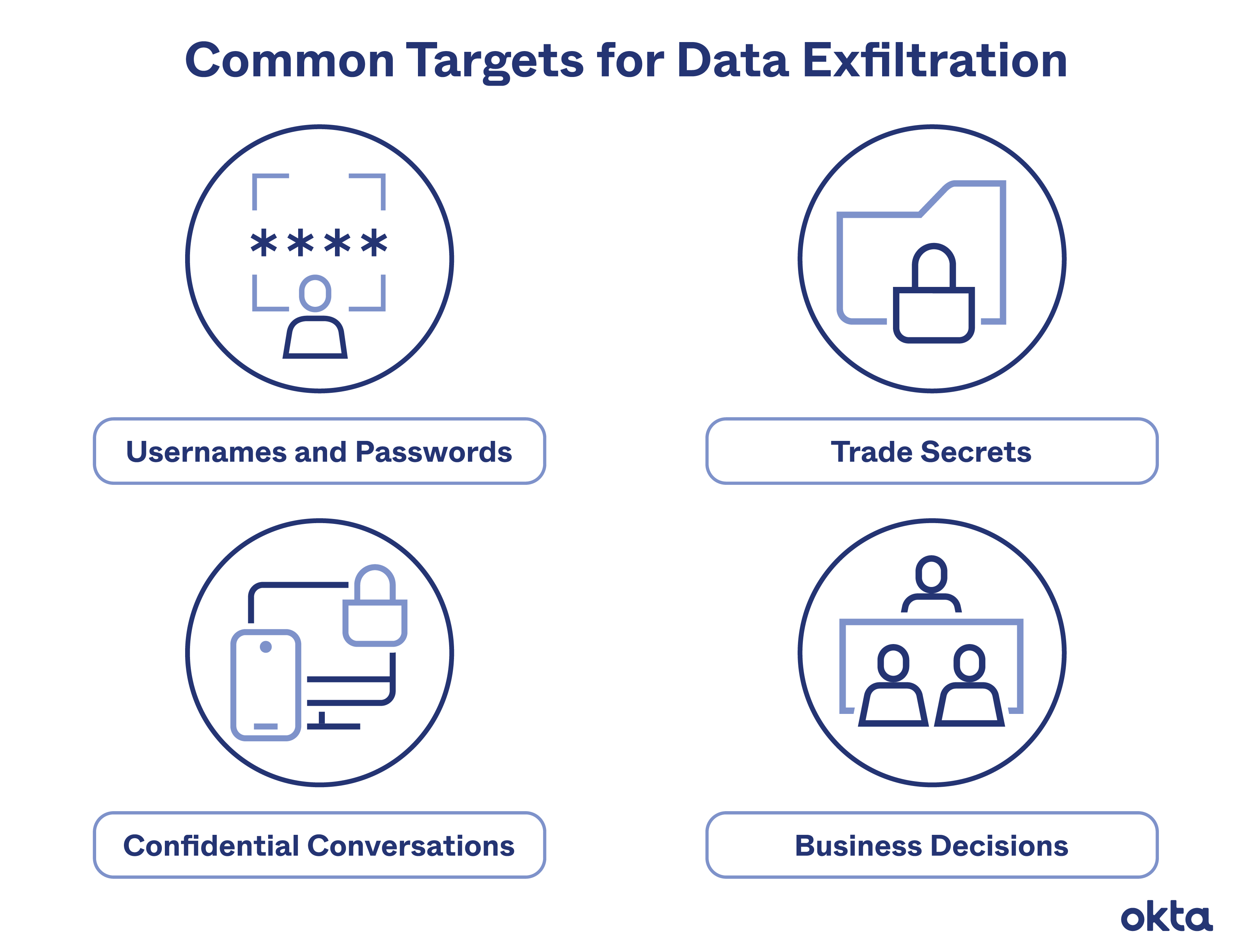
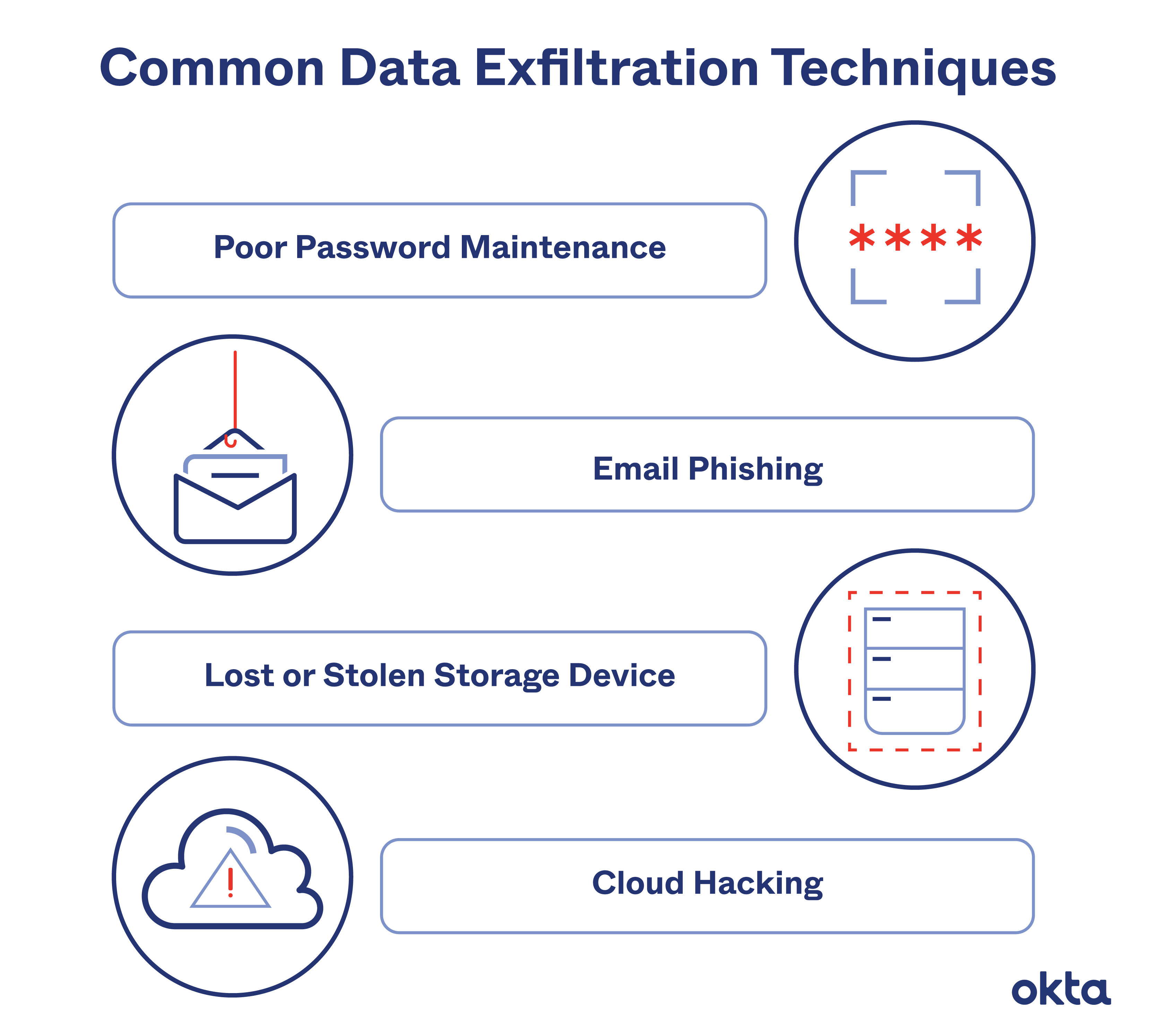
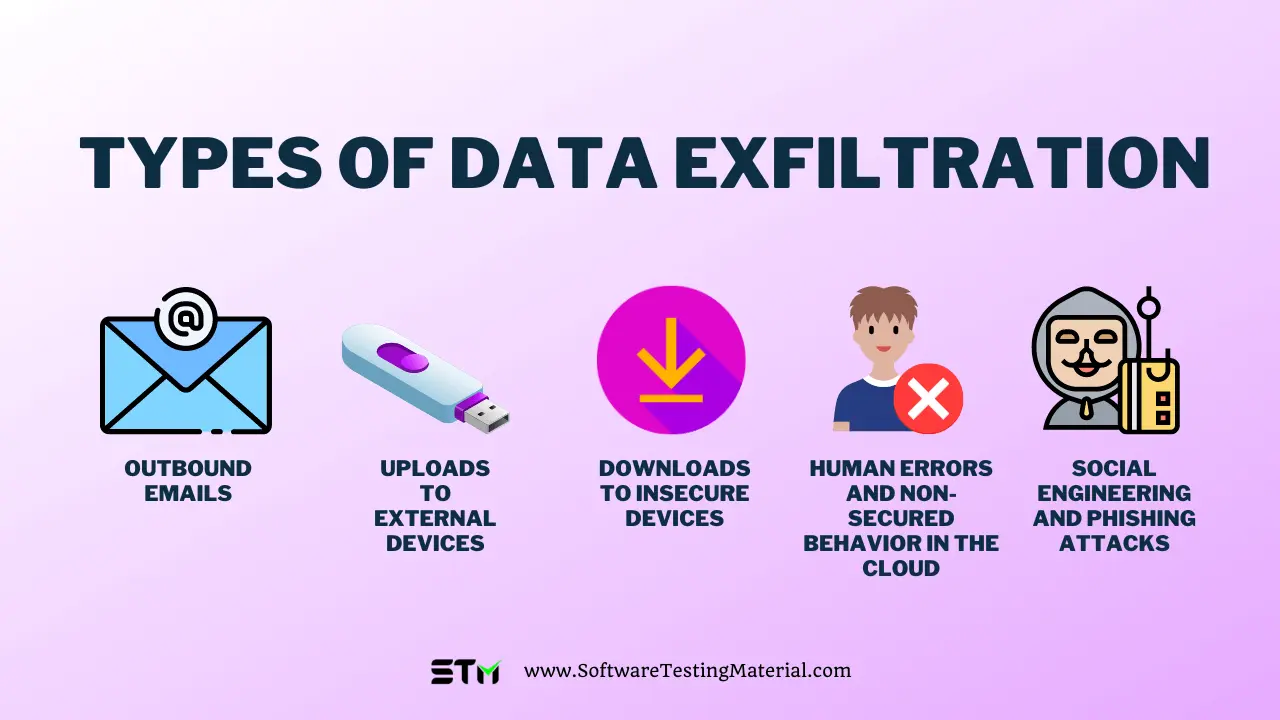
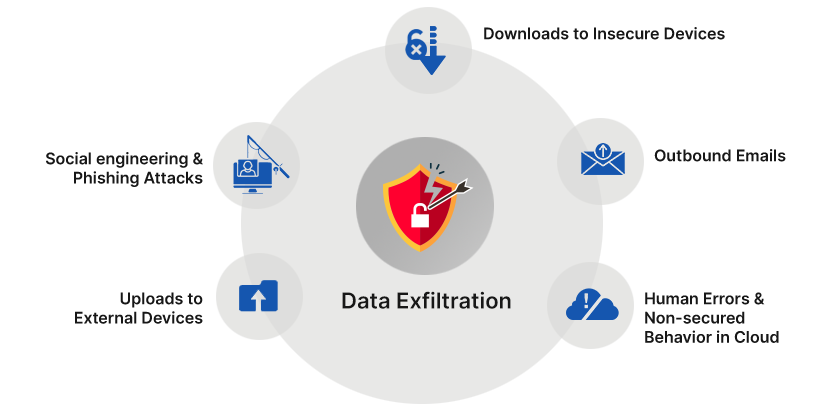
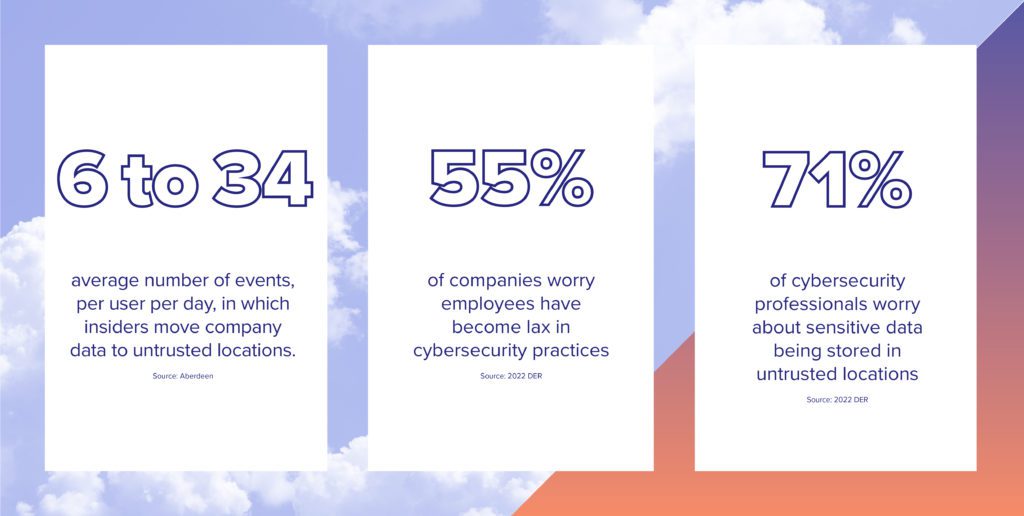
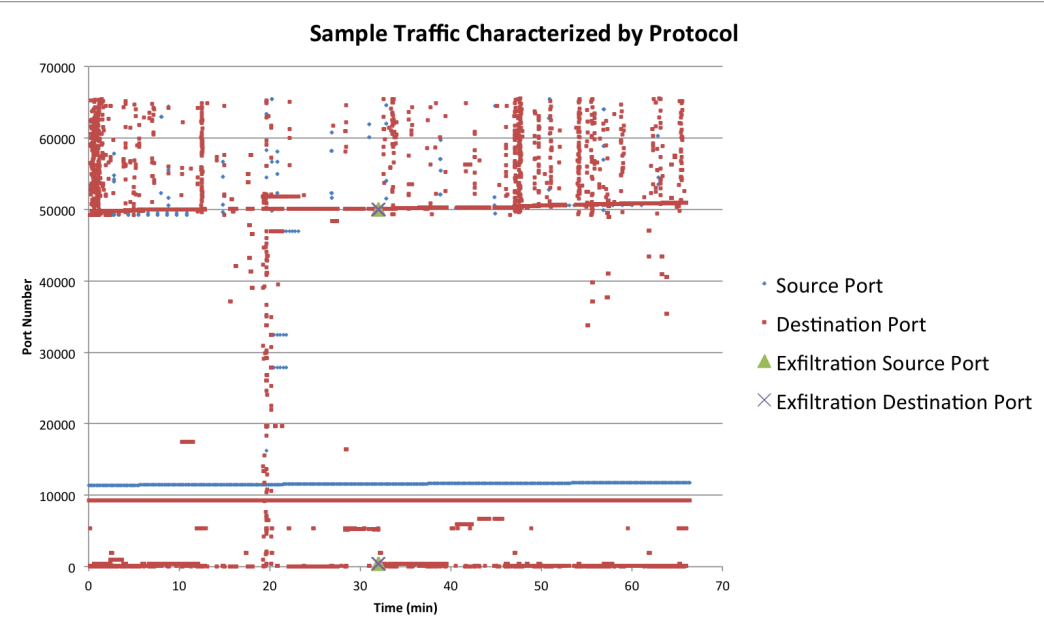
Data exfiltration is the theft or unauthorized removal or movement of any data from a device. Discover the different data exfiltration types and how Fortinet solutions can Data exfiltration—also known as data extrusion or data exportation—is data theft: the intentional, unauthorized, covert transfer of data from a computer or other device. Data
Data exfiltration refers to unauthorized copying, transferring, and retrieving sensitive information from a computer or network, a process that may What Is Data Exfiltration? Data exfiltration is the theft or unauthorized transfer of data from a device or network. According to the Mitre ATT&CK Framework, “once they’ve
Related Posts of What Is Data Exfiltration :
Data Exfiltration Definition Damage amp Defense Okta
What Is Data Exfiltration Active Intel Investigations
Top 10 Proactive Measures to Prevent Data Exfiltration Pathlock
Data Exfiltration Definition Damage amp Defense Okta
Data Exfiltration What is It and How to Protect Yourself
Data Exfiltration What is It and How to Protect Yourself
Data Exfiltration The Silent Threat Undermining Your Security
Preventing Data Exfiltration ThreatLocker
What Is Data Exfiltration Examples Detection amp Prevention
What Is Data Exfiltration Definition How To Prevent It amp More Code42
12 Real world examples of data exfiltration
What Is Data Exfiltration And the Best Way to Prevent It StrongDM
What is data exfiltration Common Methods and Attacks
What is Data Exfiltration Definition How To Prevent
What is Data Exfiltration Definition How To Prevent
How to Prevent Data Exfiltration Incidents Reflectiz
What is Data Exfiltration Techniques amp Prevention
Learn about Data Exfiltration
Perfect Data Exfiltration Technique Demonstrated
Perfect Data Exfiltration Technique Demonstrated
7 Data Exfiltration Techniques and How to Avoid Them Netwoven
7 Data Exfiltration Techniques and How to Avoid Them Netwoven
What s your Data Exfiltration Strategy
Prevent Data Exfiltration The Complete Guide Endpoint Protector
Prevent Data Exfiltration The Complete Guide Endpoint Protector
Prevent Data Exfiltration The Complete Guide Endpoint Protector
Prevent Data Exfiltration The Complete Guide Endpoint Protector
Data Exfiltration Prevention with SASE ThreatsHub Cybersecurity News
What Is Data Exfiltration And the Best Way to Prevent It StrongDM
Data Exfiltration What Does it Mean and How to Prevent it
Data Exfiltration What Does it Mean and How to Prevent it
Can t Touch This Data Exfiltration via Finger
What is Data Exfiltration and How Can You Prevent It Fortinet
What Is Data Exfiltration Prevention And Protection
What is Data Exfiltration Definition how to prevent it amp more Code42
Data Exfiltration What It Is and How to Prevent It Mimecast
What is Data Exfiltration Meaning amp Prevention Noname Security
Data Exfiltration Meaning Examples amp How to Prevent It Ekran System
What is Data Exfiltration The Silent Digital Network Threat
Data Exfiltration 101 How Threat Actors Compromise Networks Keyboard
How to detect data exfiltration 5 steps
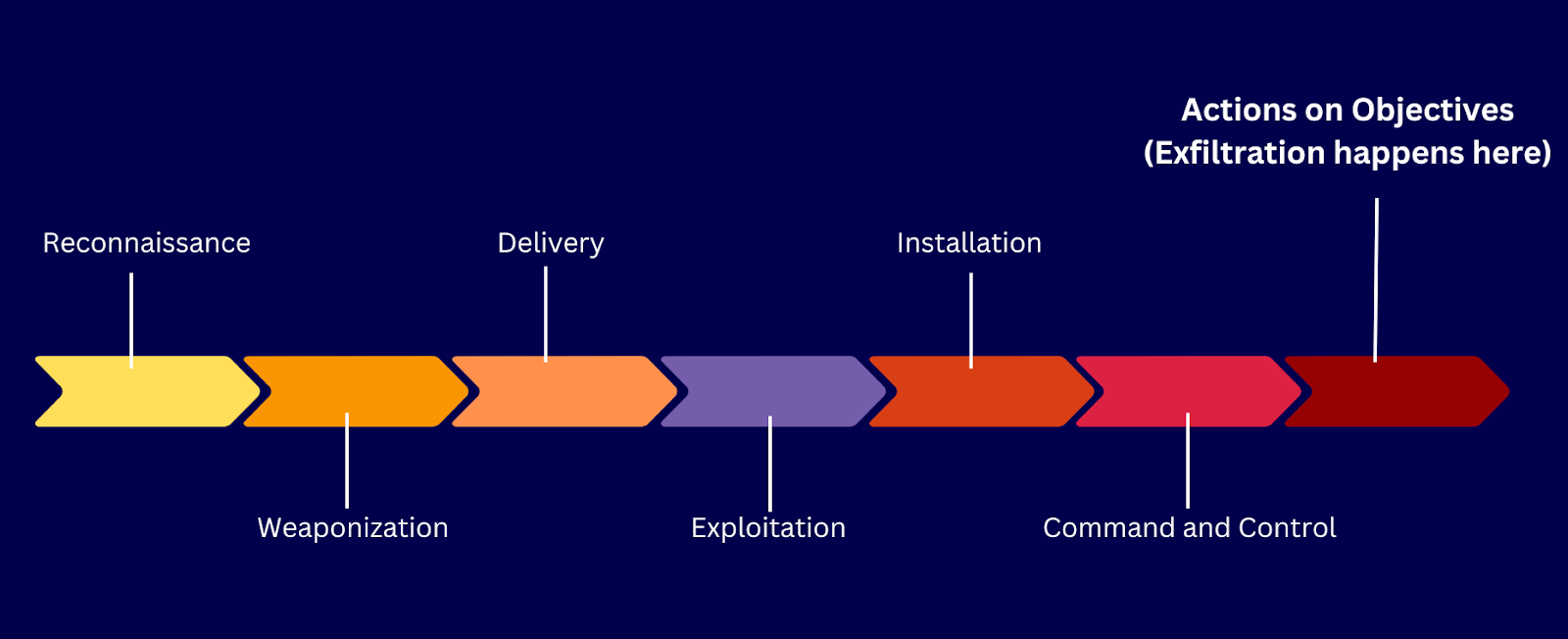
What Is Data Exfiltration MITRE ATT amp CK 174 Exfiltration Tactic TA0010
What is Data Exfiltration Plus 3 Tips to Prevent It
What is Data Exfiltration 5 Key Facts Free Checklist
Preventing data exfiltration with Logpoint
What Is Data Exfiltration RiskXchange
Anatomy of a Data Exfiltration Investigation Magnet Forensics
What Is Data Exfiltration MITRE ATT amp CK 174 Exfiltration Tactic TA0010
What is Data Exfiltration Plus 3 Tips to Prevent It
What is Data Exfiltration 5 Key Facts Free Checklist
Preventing data exfiltration with Logpoint
What Is Data Exfiltration RiskXchange
Anatomy of a Data Exfiltration Investigation Magnet Forensics
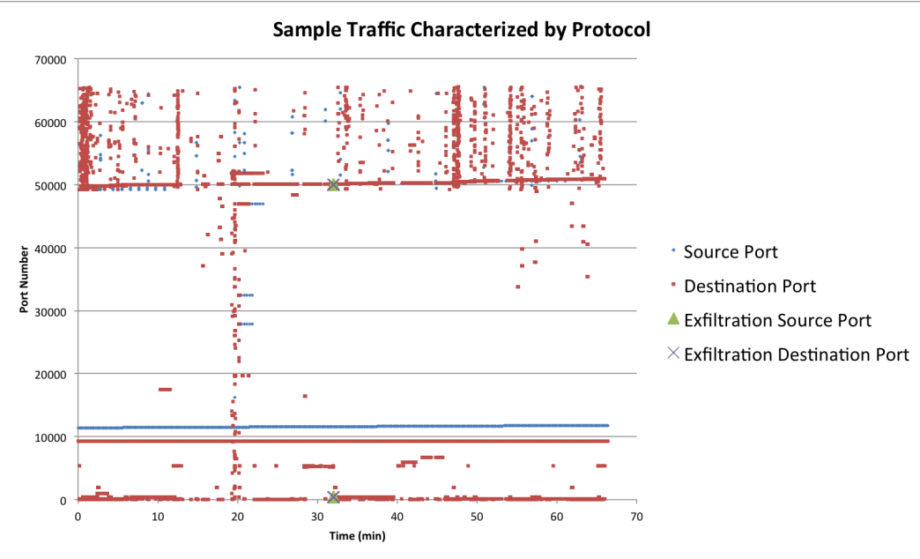
Detecting Data Exfiltration White Paper Mustek
Conducting and Detecting Data Exfiltration Protect your organization
Conducting and Detecting Data Exfiltration Protect your organization
Understanding Data Exfiltration Key Concepts Explained Cybersecurity
How Machine Learning is Vital in Successful Data Exfiltration Detection
What is Data Exfiltration How It Works Best Practices amp More Zeguro
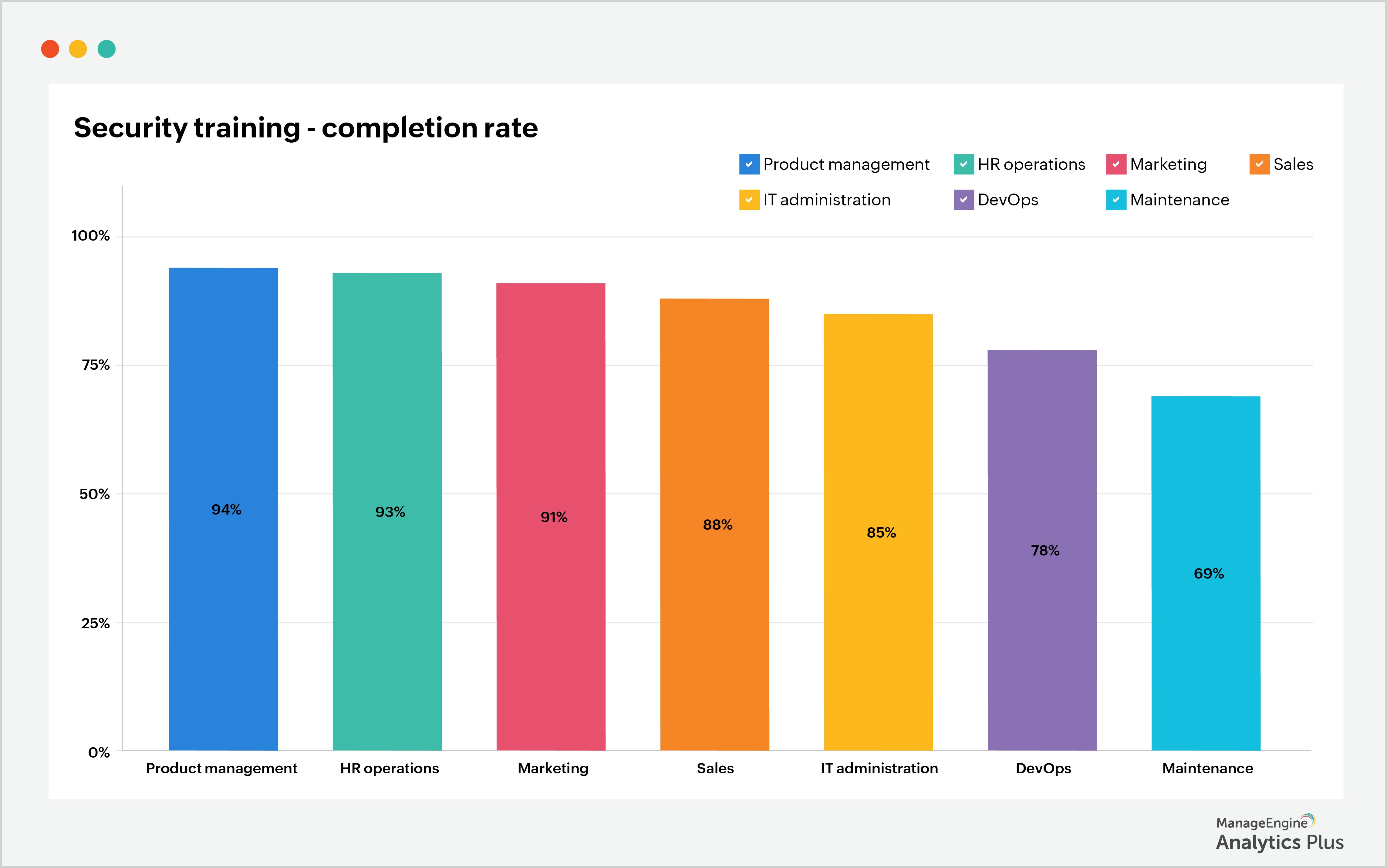
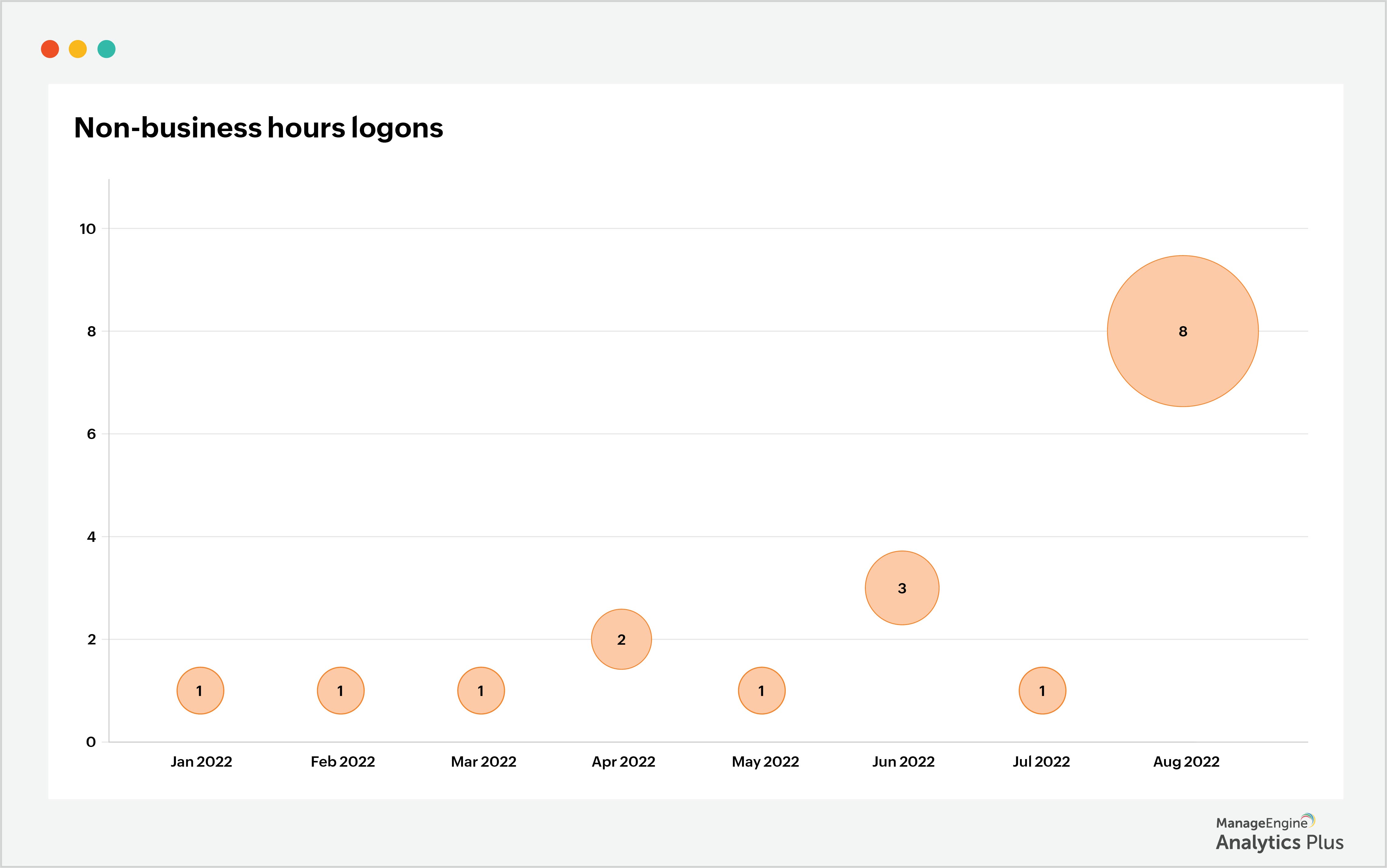
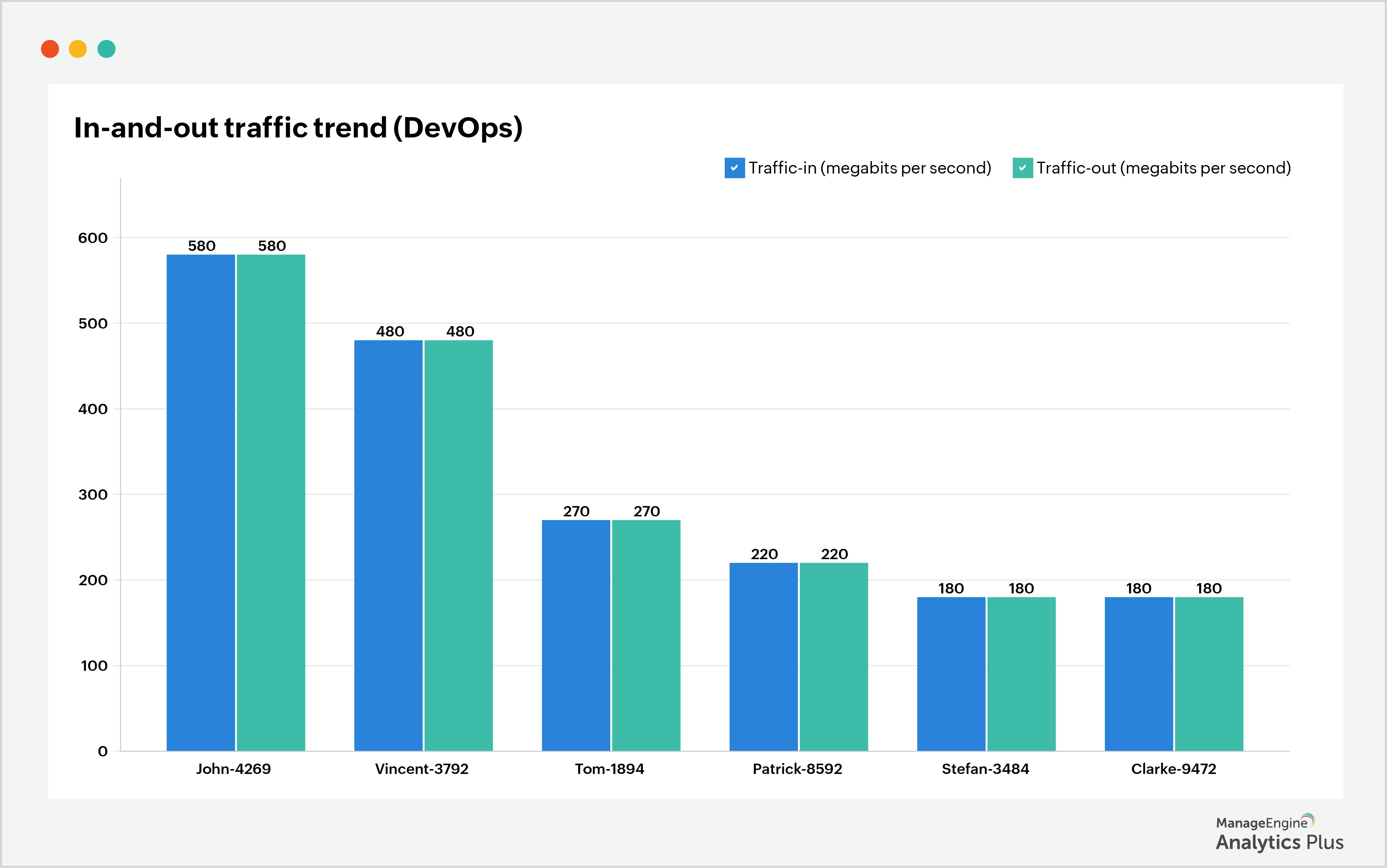
What is Data Exfiltration and how to prevent it using analytics IT
What is Data Exfiltration and how to prevent it using analytics IT
What is Data Exfiltration and how to prevent it using analytics IT
What is Data Exfiltration and how to prevent it using analytics IT
The Data Exfiltration Techniques You Need to be Aware of BlackFog
The Data Exfiltration Techniques You Need to be Aware of BlackFog
How to Block Data Exfiltration Before It Becomes a Full Blown Breach
The Rise of Data Exfiltration and Why It Is a Greater Risk Than Ransomware
What is Data Exfiltration and how it can be countered by companies
What is Data Exfiltration and how it can be countered by companies
Why Exfiltration of Data is the Biggest Cyberthreat Facing Your
Managing Data Exfiltration Risks with Open Access in Higher Ed EdTech
Hackers used data exfiltration based on video steganographySecurity Affairs
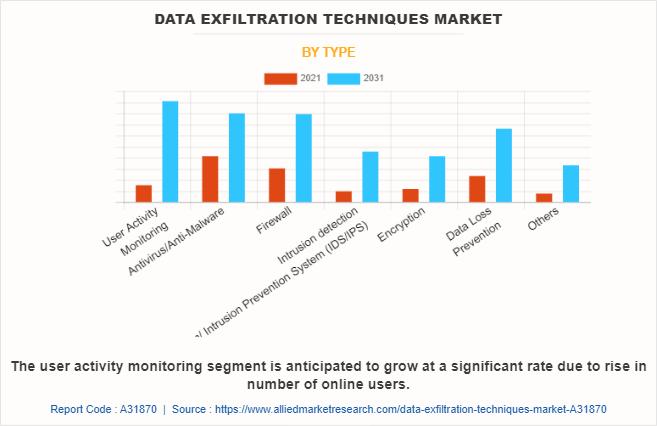
Data Exfiltration Techniques Market is forecasted to achieve
What is data exfiltration and how to prevent it
What Is Data Exfiltration Definition How To Prevent It amp More
What Is Data Exfiltration - The pictures related to be able to What Is Data Exfiltration in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.