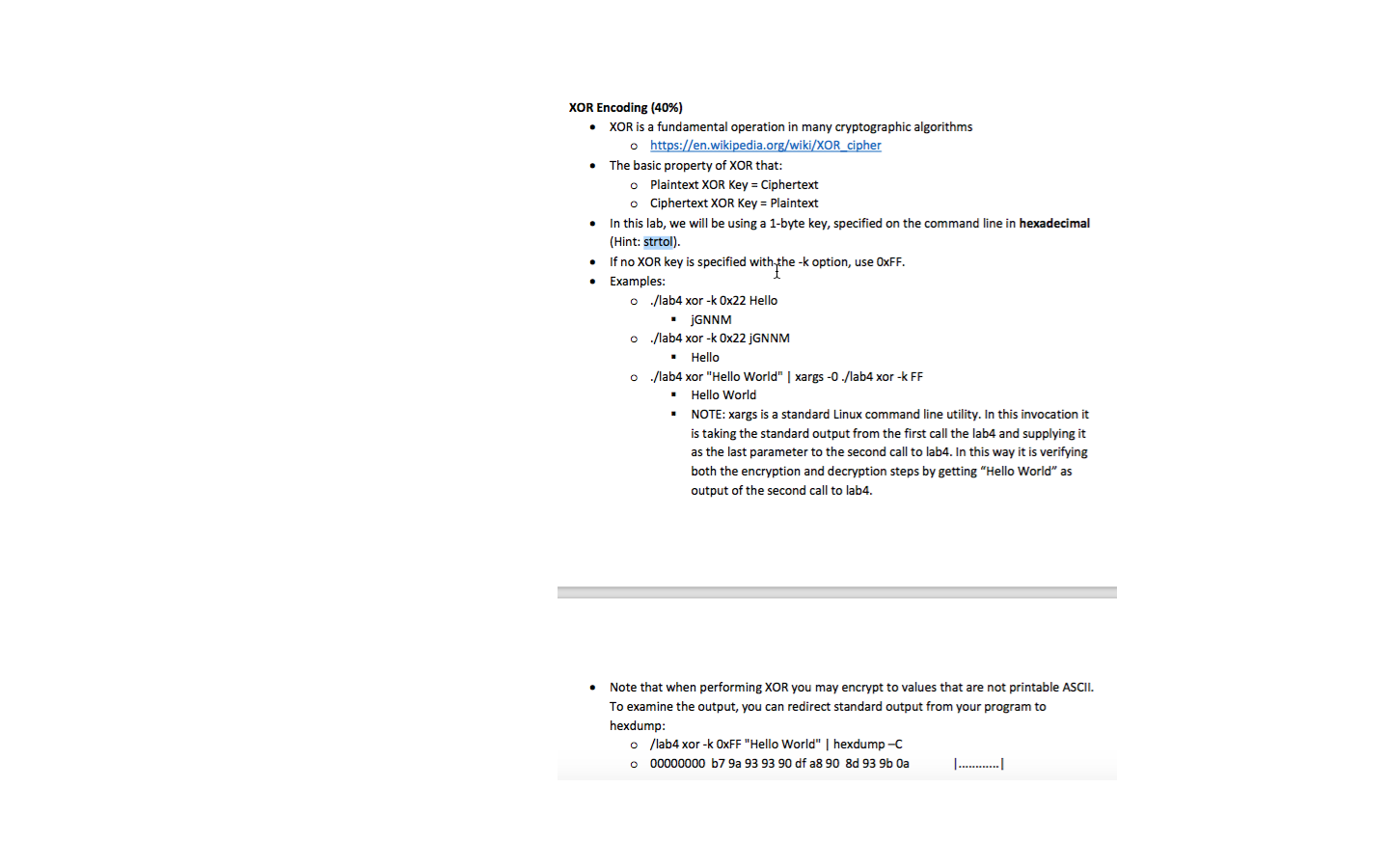
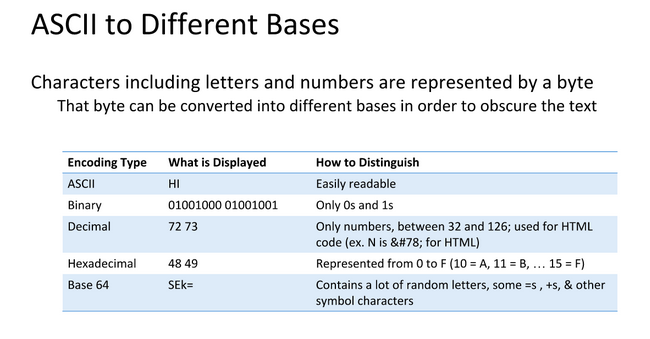
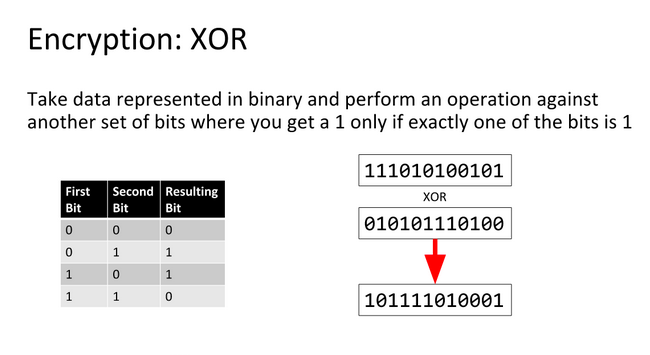
xor crypt examples CodeSandbox
XOR Meaning 187 Slang term definition amp example usage 187 Slang org
How Does XOR Cipher Work XOR Chipher Encryption by Logsign Medium
Why is Exclusive Or XOR Important in Cryptography by Lane Wagner
Why Is XOR the Perfect Cipher HackerNoon
Deciphering Single byte XOR Ciphertext
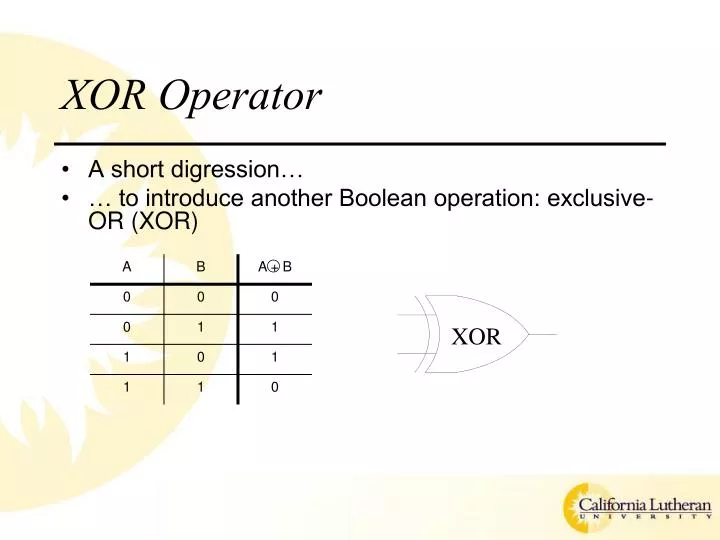
PPT XOR Operator PowerPoint Presentation free download ID 4175144
Symbol of XOR Unlocking the Secrets of the Exclusive OR
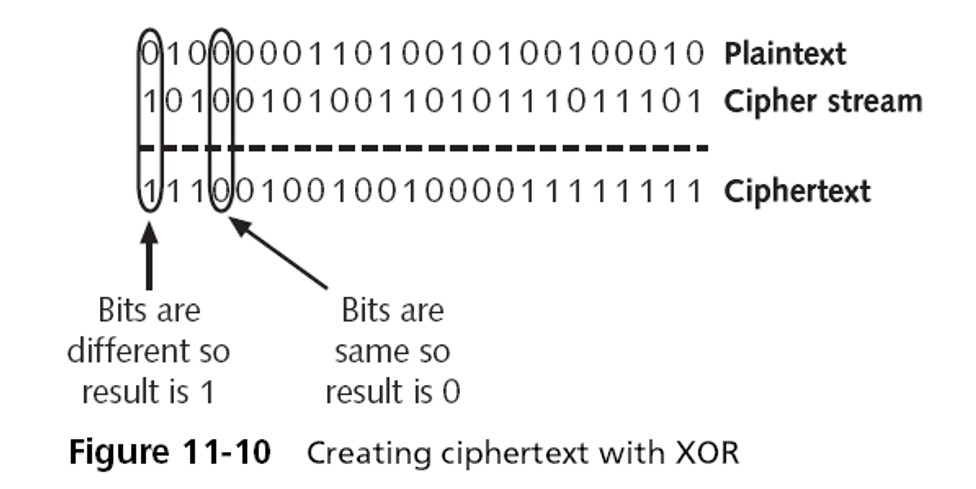
Cryptography stream ciphers
GitHub leschiffres xor encryption An algorithm to find the
PPT XOR Operator PowerPoint Presentation free download ID 4175144
XOR Encryption by Shifting Plaintext GeeksforGeeks
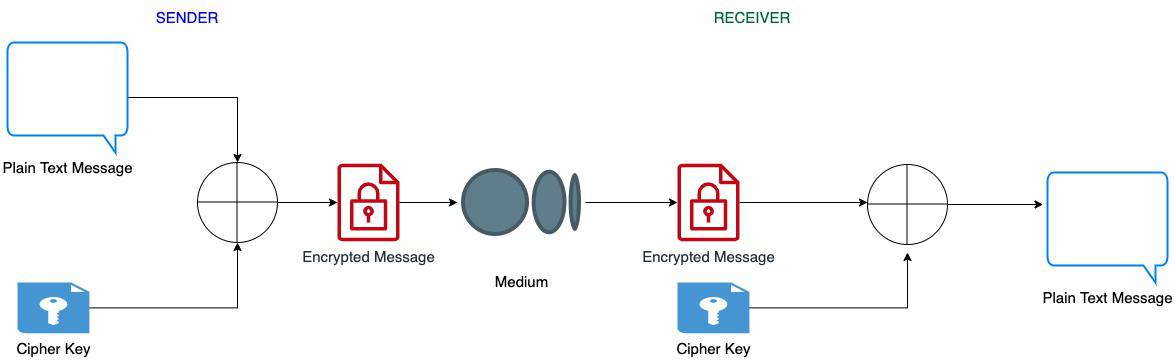
XOR Encryption and Decryption
SOLUTION Encryption xor operation Studypool
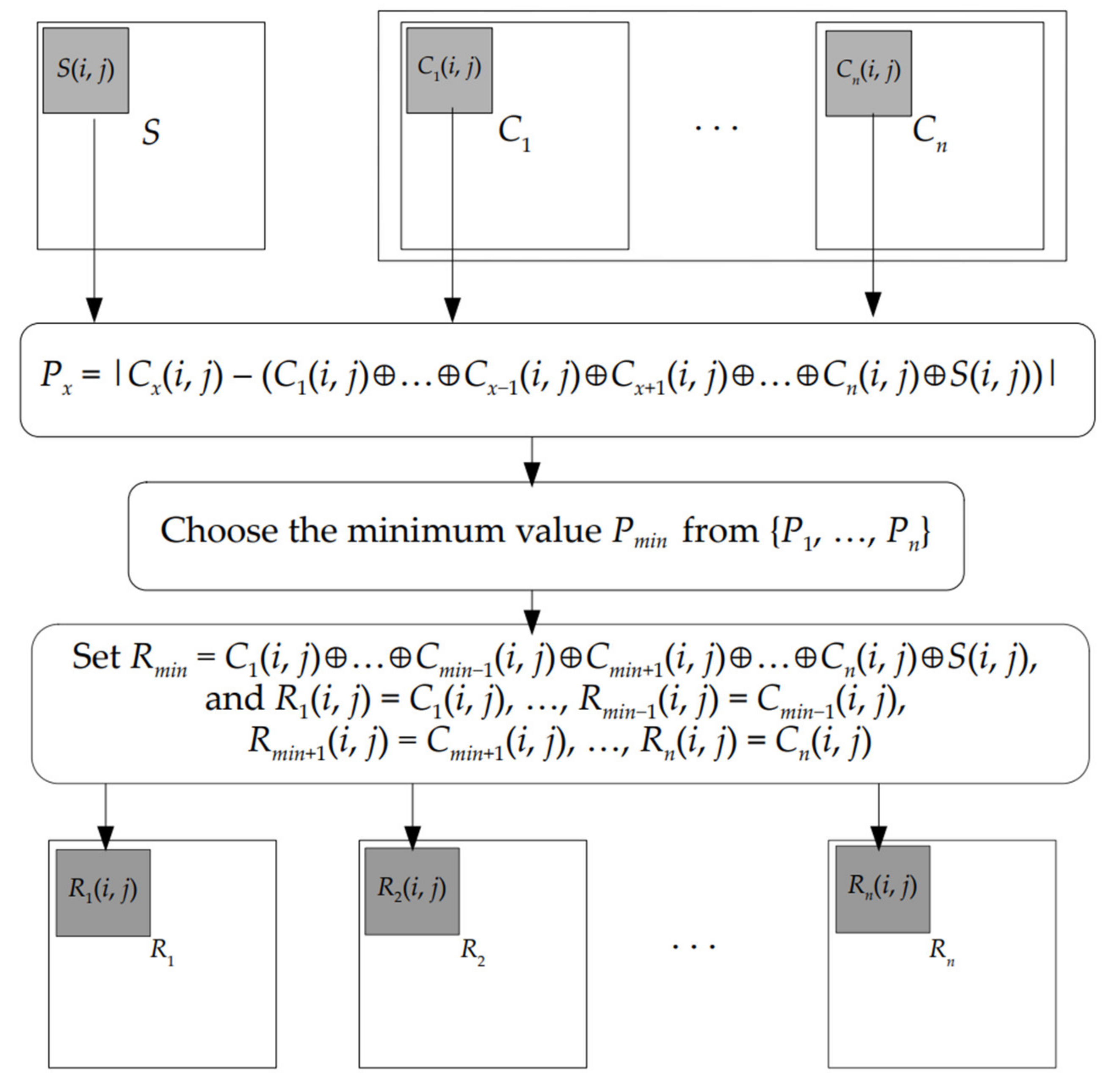
Flowchart showing Improved XOR decryption Algorithm Download
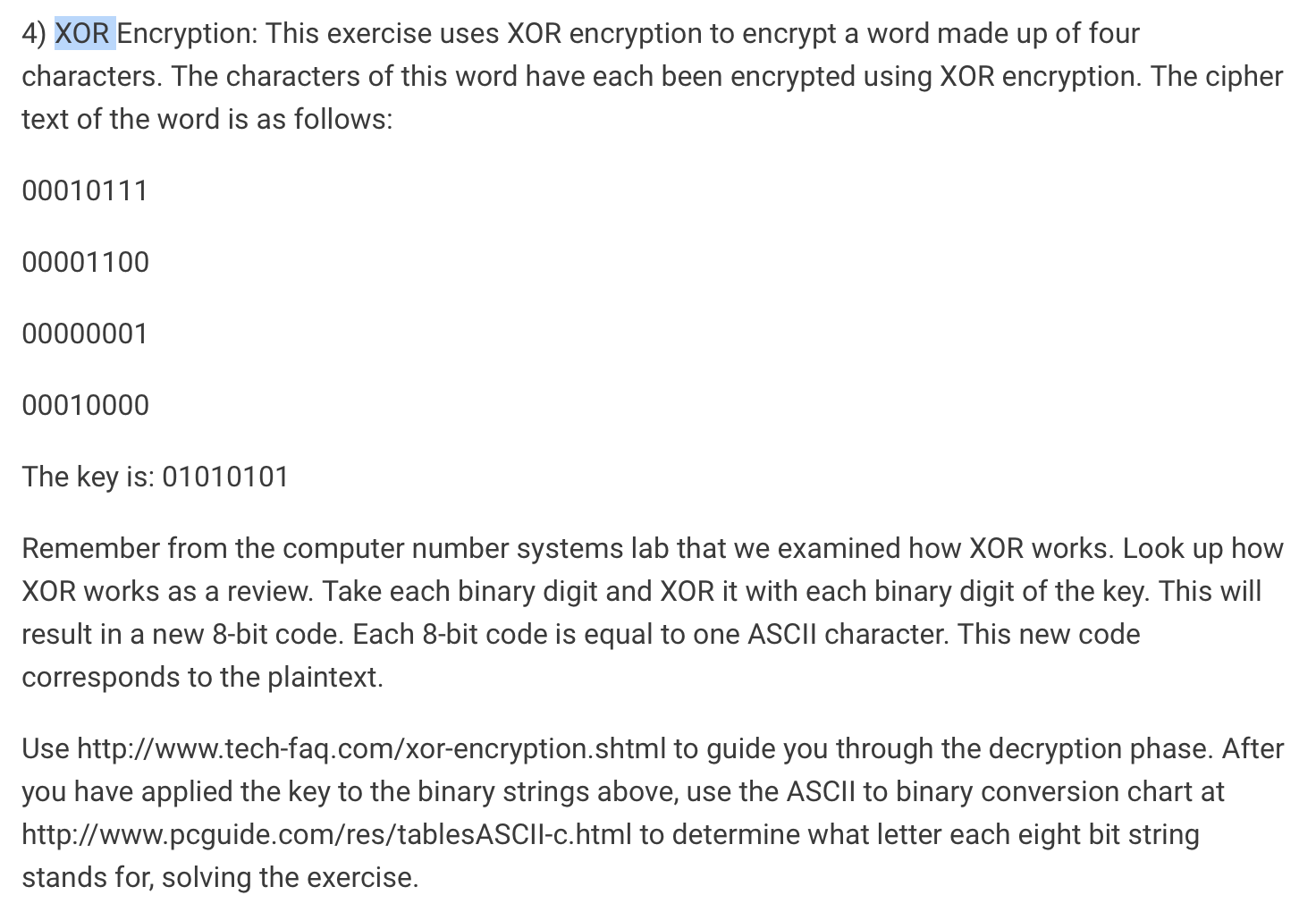
Solved 4 XOR Encryption This exercise uses XOR encryption Chegg com
Encryption implementations using a XOR based logic encryption of a
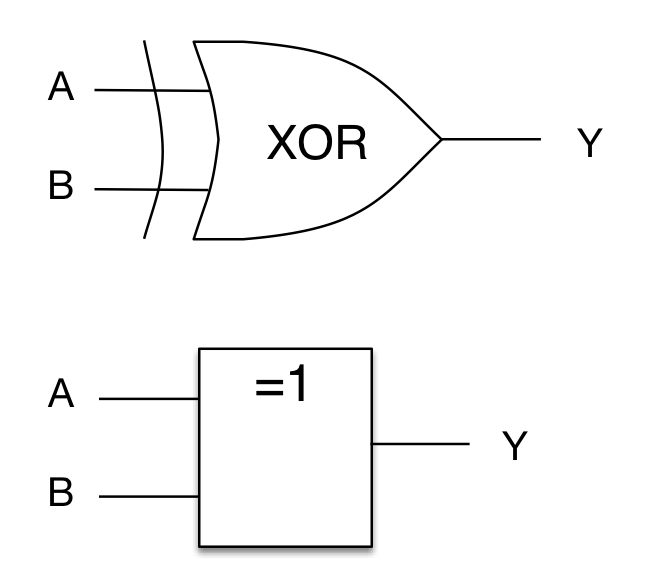
Logical XOR Glossary Entry Embedded Systems
Malware Basics Understanding the XOR Cipher by Devin Jun 2022
Solved 4 XOR Encryption This exercise uses XOR encryption Chegg com
Encryption implementations using a XOR based logic encryption of a
Logical XOR Glossary Entry Embedded Systems
Malware Basics Understanding the XOR Cipher by Devin Jun 2022
Malware Basics Understanding the XOR Cipher by Devin Jun 2022
Some examples for the XOR encryption process of different characters
Simple XOR Text Encryption and Decryption in Visual C 171 Null Byte
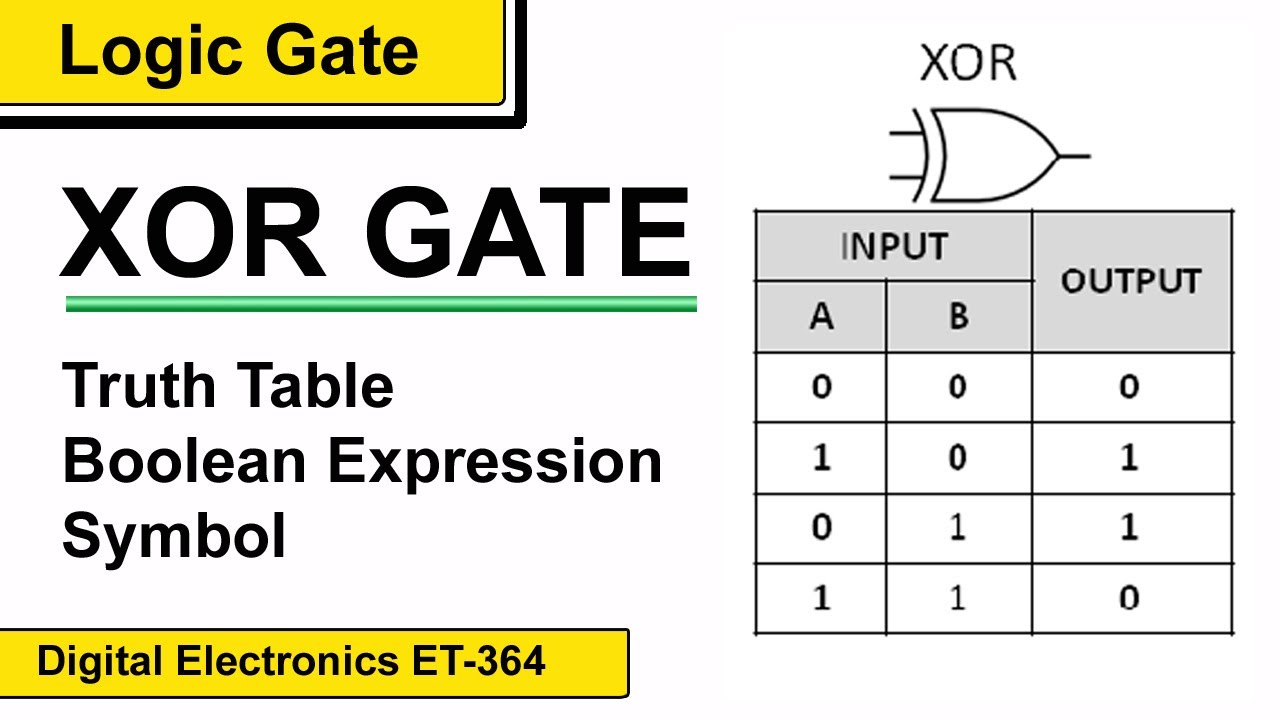
What Is Xor Gate In Digital Electronics Design Talk
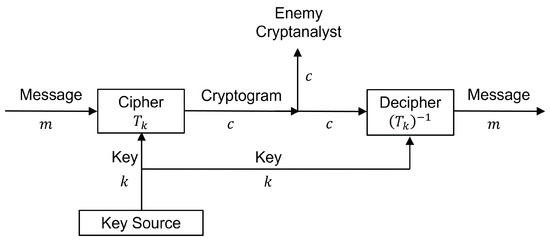
Cryptography A Closer Look at the Algorithms
187 Why XOR alone is an incredibly bad encryption technique
187 Why XOR alone is an incredibly bad encryption technique
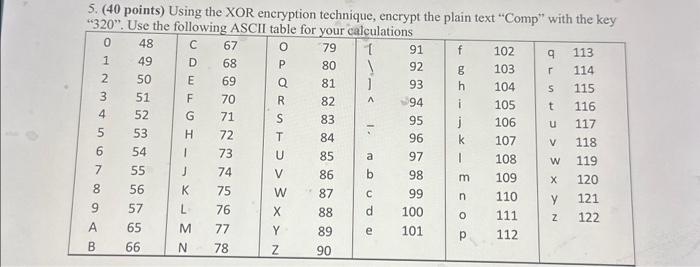
Solved 5 40 points Using the XOR encryption technique Chegg com
Images after xor of encrypted images with different keys and same keys
SOLVED The example above shows how to use the XOR operator to encrypt
why XOR is recommended Used in every paper I read for encryption and
The XOR Encryption algorithm is a effective and easy to implement
The making of the XOR cipher Mathematical proof that m m k
PPT Security in Computing Chapter 2 Elementary Cryptography
The XOR Encryption algorithm A effective and easy to implement method
Rahasia Keamanan Data dengan Cipher XOR yang Tak Terpecahkan Pintu News
Bitwise Operators 3 The XOR Operation YouTube
What does XOR mean YouTube
Symmetric Key Cryptography The XOR Cipher YouTube
XOR Encryption and Decryption Cryptography YouTube
Symmetric Key Cryptography The XOR Cipher YouTube
XOR Encryption and Decryption Cryptography YouTube
Xor Function Applied Cryptography YouTube
Cryptography 101 XOR Cipher YouTube
Xor Function Solution Applied Cryptography YouTube
Tutorial 7 Kriptografi XOR cipher dasar YouTube
Why XOR is used everywhere in Cryptography YouTube
The XOR Operation Baeldung on Computer Science
Popular mobile security app uses worthless encryption method ExtremeTech
Number Representation amp Operators ppt download
One Time Pad The Only Unbreakable Cipher ppt download
XOR cipher 183 Hyperskill
Cryptology Information Security S 252 leyman Kondakc S Kondakci ppt download
Chapter 12 amp 13 Privacy Security and Polite Society ppt download
Chapter 12 amp 13 Privacy Security and Polite Society ppt download
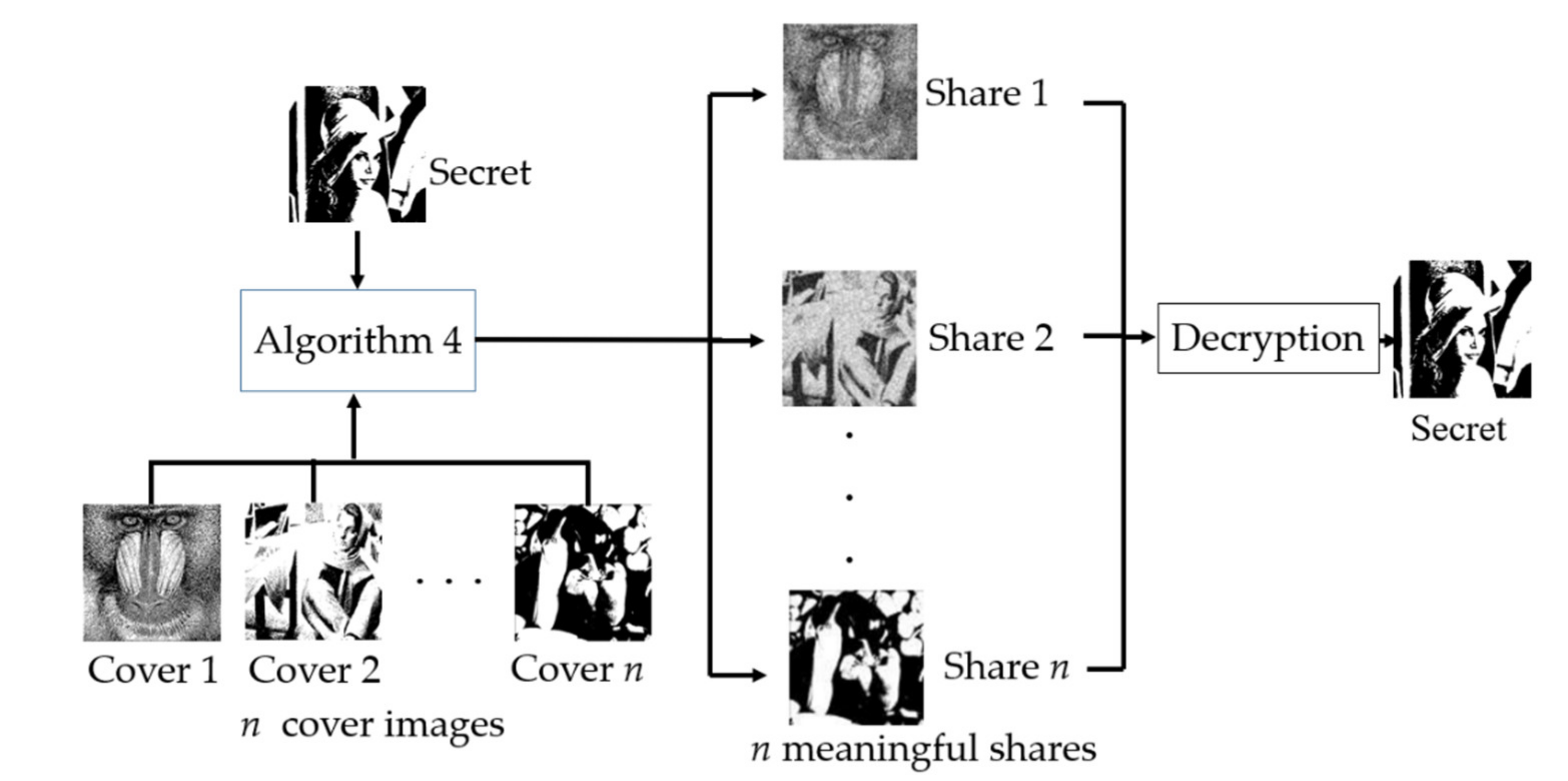
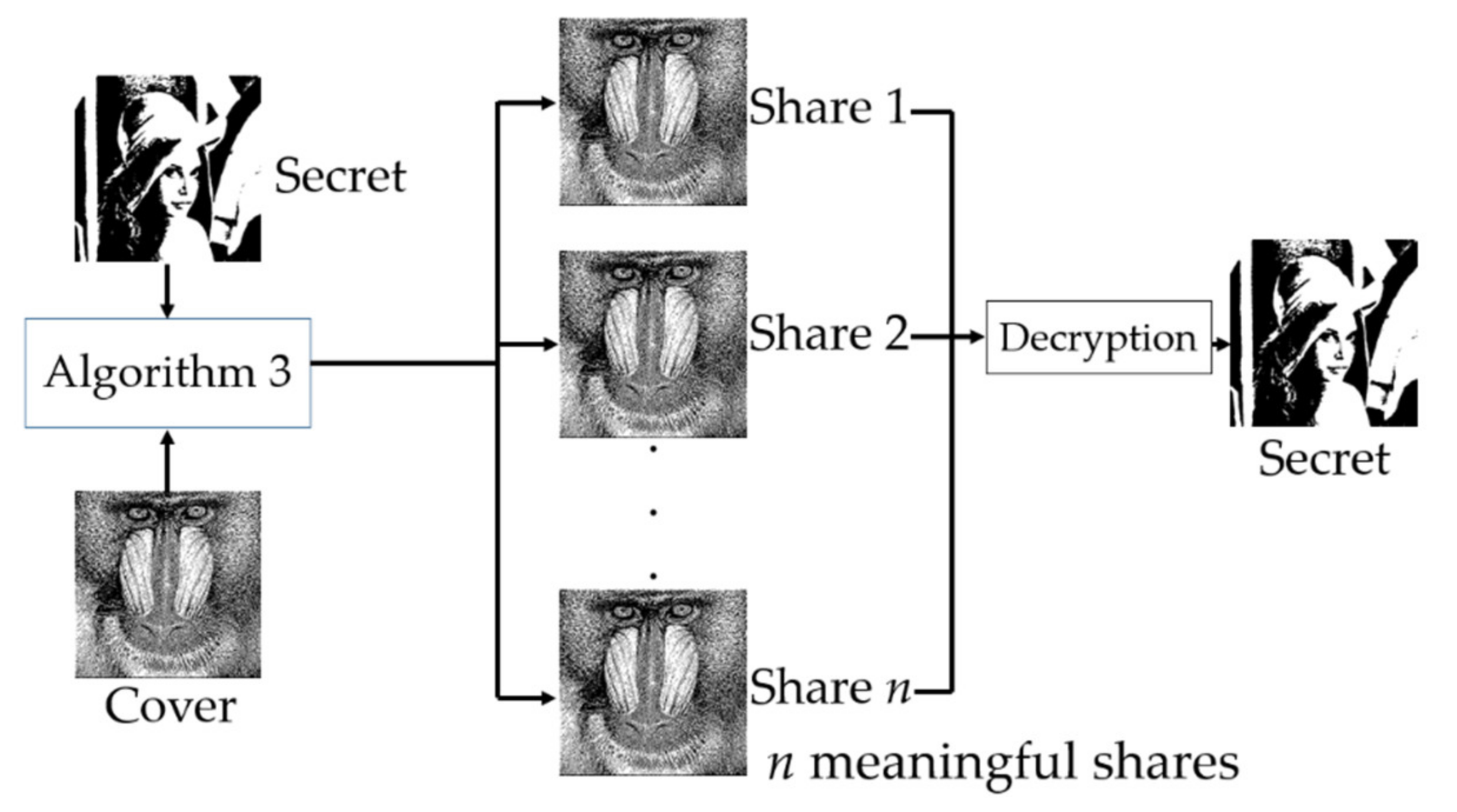
Applied Sciences Free Full Text XOR Based n n Visual
Applied Sciences Free Full Text XOR Based n n Visual
Applied Sciences Free Full Text XOR Based n n Visual
Applied Sciences Free Full Text XOR Based n n Visual
Cryptography Dr A Clune The Computing Service University of York
Cryptography Dr A Clune The Computing Service University of York
Cryptography Dr A Clune The Computing Service University of York
TELE3119 Trusted Networks Week 1 ppt download
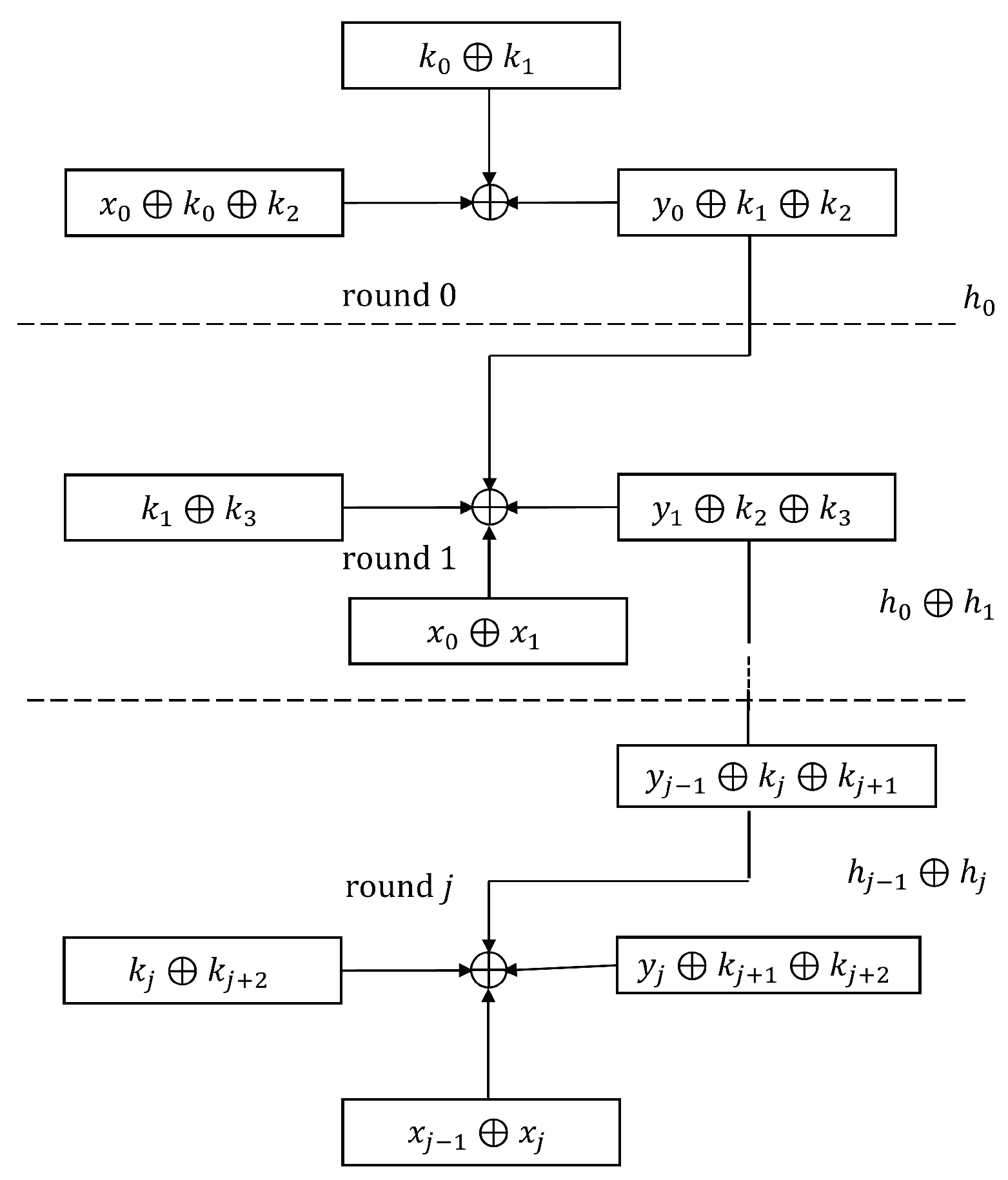
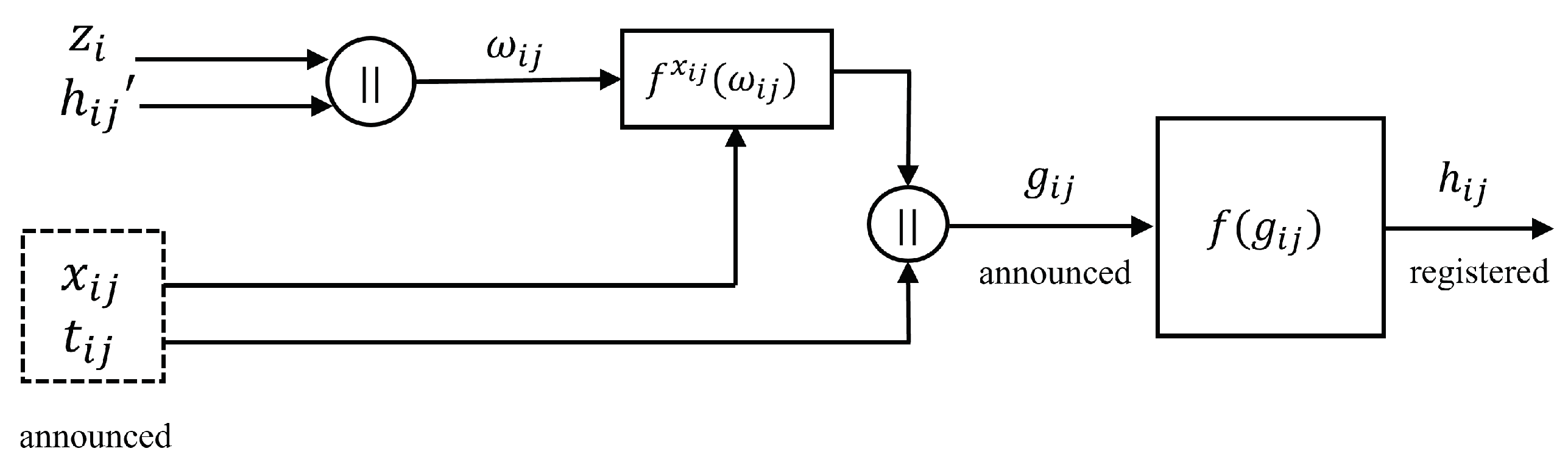
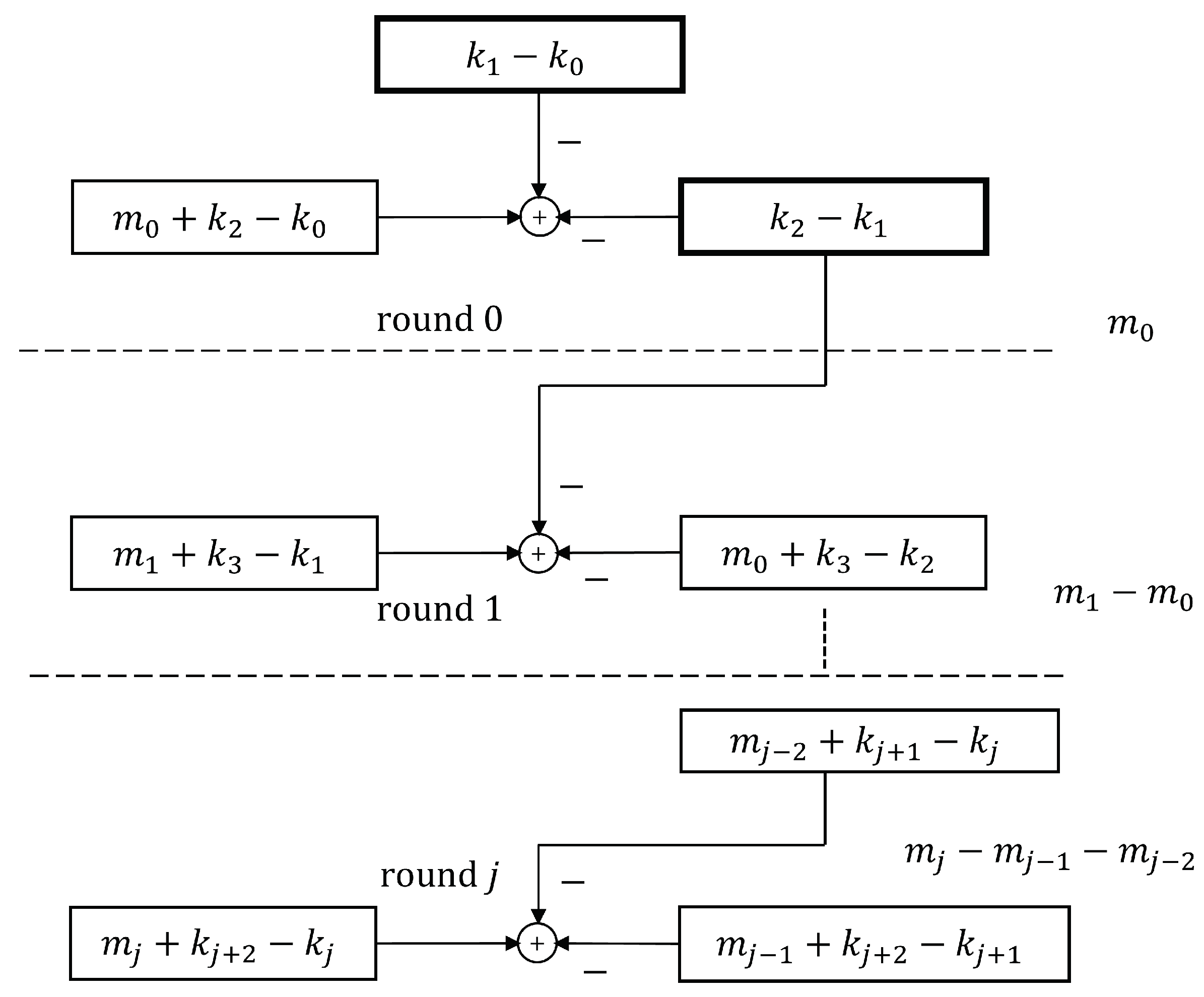
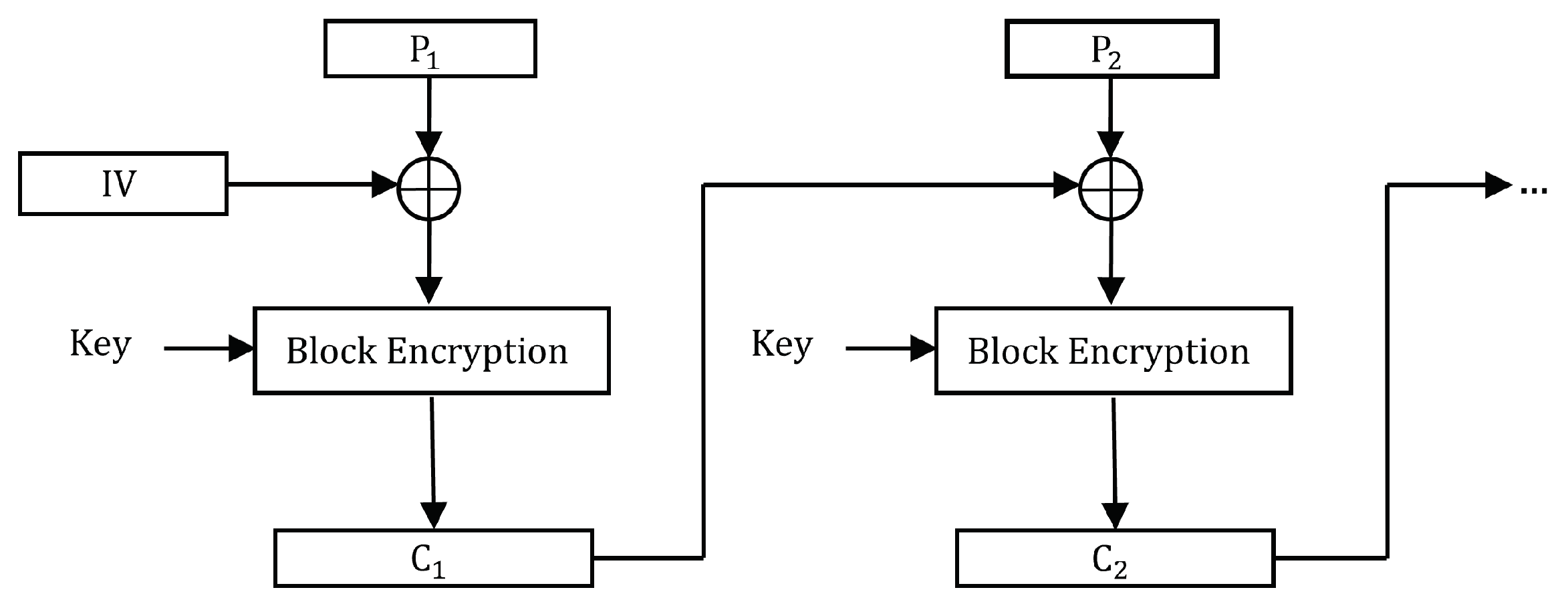
Cryptography Free Full Text XOR Chain and Perfect Secrecy at the
Cryptography Free Full Text XOR Chain and Perfect Secrecy at the
Cryptography Free Full Text XOR Chain and Perfect Secrecy at the
Cryptography Free Full Text XOR Chain and Perfect Secrecy at the
Cryptography Free Full Text XOR Chain and Perfect Secrecy at the
What Does Xor Mean In Cryptography - The pictures related to be able to What Does Xor Mean In Cryptography in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.